Computer Use Reporter Alternatives for Windows
Do you want to find the best Computer Use Reporter alternatives for Windows? We have listed 23 Security that are similar to Computer Use Reporter. Pick one from this list to be your new Computer Use Reporter app on your computers. These apps are ranked by their popularity, so you can use any of the top alternatives to Computer Use Reporter on your computers.
Top 23 Software Like Computer Use Reporter - Best Picks for 2025
The best free and paid Computer Use Reporter alternatives for windows according to actual users and industry experts. Choose one from 23 similar apps like Computer Use Reporter 2025.
Decrap my Computer
Uninstall unwanted software applications, clean up the Windows registry, and delete unused desktop items using this approachable toolDesigned for PC cleaning and maintenance, Decrap my Computer is an easy-to-use application that enables you to uninstall unwanted software that take...
Computer Fitness
A straightforward and reliable software application that allows parents to control the time their children spend on the computer per dayComputer Fitness comes across as an aid for parents who want to limit the time kids spend on the...
Block Certain Websites On Your Computer Software
Simplistic piece of software that helps you block a user-defined list with URLs/IP addresses, upload the information from a plain text file, and set up a master passwordBlock Certain Websites On Your Computer Software is a small Windows application...
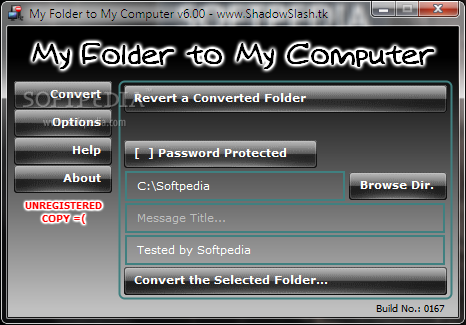
My Folder to My Computer
A program designed to give users the option to secure their personal files in a folder that would be converted What's new in My Folder to My Computer 6.01: Just a patch for a bug in the version 6.00...
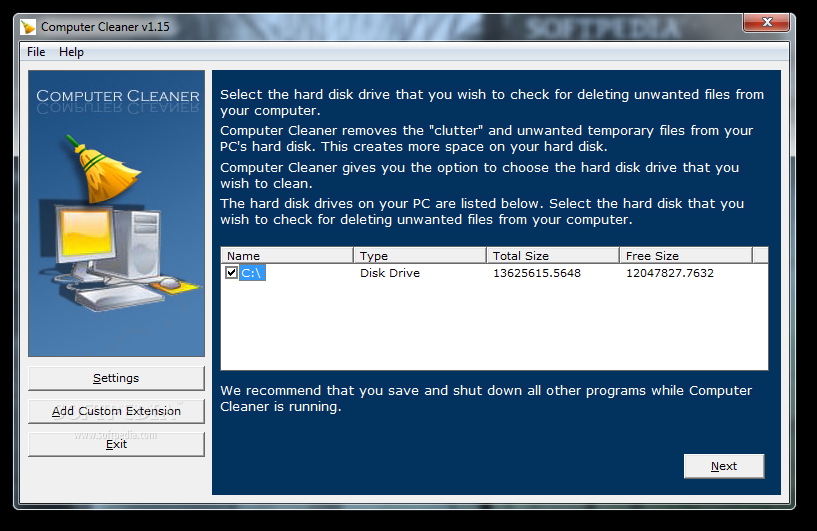
Computer Cleaner
This is an effective PC cleanerComputer Cleaner is a simple piece of software developed to help users get rid of unnecessary files and thus save space on the hard disks.As compared to other similar programs on the market, Computer...
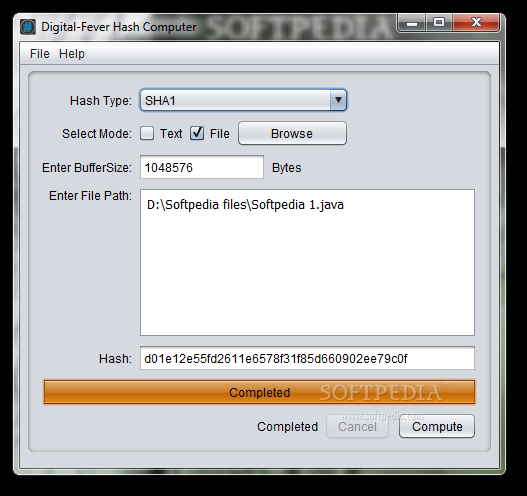
Digital-Fever Hash Computer
Calculate MD5, SHA1 and MD2 hashes of files and text using this Java-based utility dedicated to all types of users, even beginners What's new in Digital-Fever Hash Computer 1.0.1: General performance improvements Read the full changelog Digital-Fever Hash...
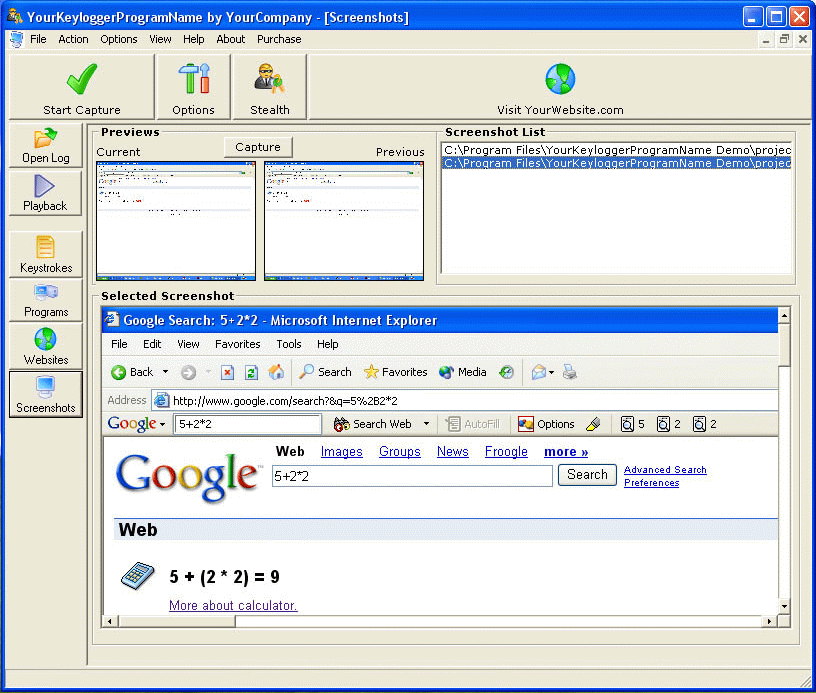
Computer Monitor Keylogger
Computer Monitor Keylogger - Secretly monitor all activity on your computerComputer Monitor Keylogger will monitor all activity on your computer, capturing programs, keystrokes, internet explorer websites and screenshots.Completely invisible and easy to use, all information captured is stored in...
OSAS Computer Locker
A simple-to-use yet efficient software tool that helps you lock down your desktop by setting up passwords, and block other users' access for a certain timeOSAS Computer Locker is a lightweight software application built specifically for helping you lock...
Process Guard
Secure your system and security programs from being attacked by other processesSecuring your computer is a more difficult job than you'd be tempted to believe and installing an antivirus or a firewall is not at all enough to stay...
ESET Internet Security
ESET's advanced internet security solution that provides local protection and can help safeguard your devices and personal data on the webMalware and Internet threats, in general, are becoming more and more relentless, especially in the context of an exponentially...

Trend Micro Maximum Security
Safeguards against email phishing scams, blocks viruses and dangerous links optimizes computer performance and restricts or filters kids’ access to websitesTrend Micro Maximum Securityis a straightforward and complete software solution worth having when you need to protect your computer...
NETGATE Internet Security
Software suite that includes a powerful firewall with advanced settings as well as an antivirus, anti-spyware and anti-spam applicationIf you do not have enough PC skills to manually protect your computer against online malware threats and unauthorized connections, you...
1st Security Agent Pro
Professional password-protected security utility to secure Windows PC. What's new in 1st Security Agent Pro 9.6: New Windows 7 tweaks added. Read the full changelog 1st Security Agent Pro is a professional password-protected system security utility to secure...
Folder Security
A simple and efficient software solution that can help you restrict the access to your more sensitive folders, with a user-defined password IMPORTANT NOTICE What's new in Folder Security 1.0.2: Hiding a folder behind a picture and audio...
1st Security Center Pro
You can configure your computer's security settings and restrict access to various features by using this intuitive software solutionSystem administrators often need to restrict access to various system features and functions in order to secure their machines or protect...
Endpoint Security Manager
Centralized management tool for all your endpoint security needs.Comodo Endpoint Security Manager (CESM) enables the remote, centralized management of end-point security products such as Comodo Internet Security on corporate workstations. With Comodo Endpoint Security Manager you will save time,...
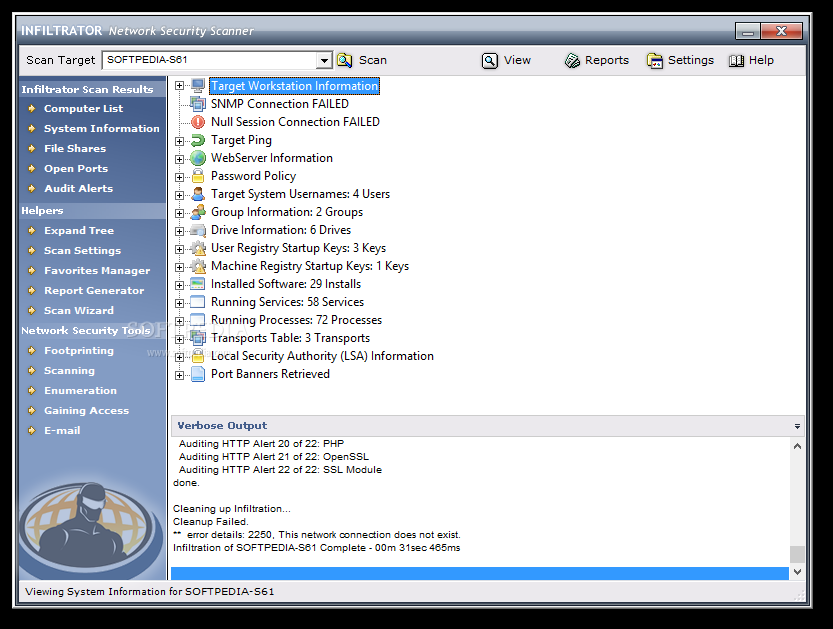
Infiltrator Network Security Scanner
A Network Security Scanning and Auditing SuiteInfiltrator Network Security Scanner can quickly audit your network computers for possible vulnerabilities, exploits, and information enumerations.It comes with a built-in database of known vulnerabilities, that can be updated online and allows you...

Maui Security Scanner
Maui Security Scanner allows you to scan for specific vulnerabilities, such as Fault Injection, SQL Injection and XSSMaui Security Scanner is an innovative security assessment software suite for today's sophisticated Web application environments..Maui Security Scanner ensures the security of...
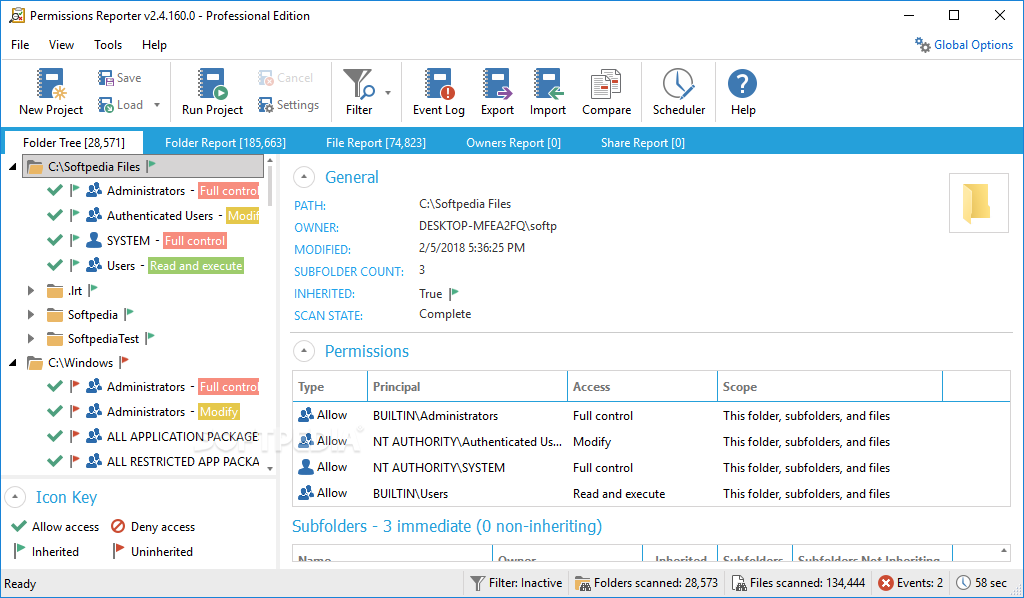
Permissions Reporter
Manage file system permissions much easier with this application, which displays the permission level of all types of users for all the folders you select What's new in Permissions Reporter 3.0.301.0: Fixed regression that could trigger crash during UI...
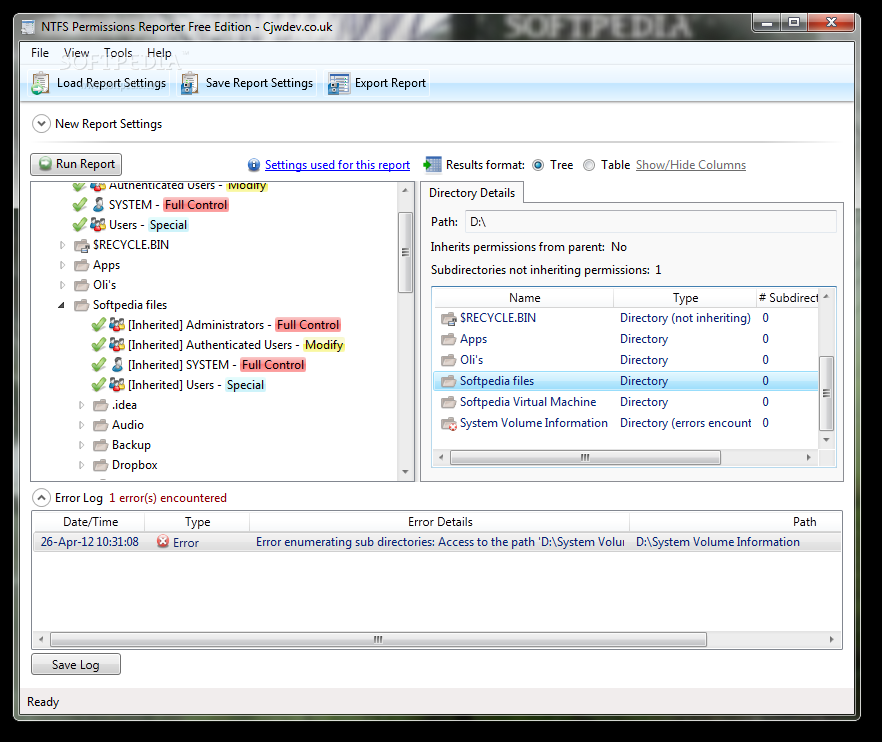
NTFS Permissions Reporter
A reporting utility for easily viewing NTFS permissions What's new in NTFS Permissions Reporter 1.0.1.0: Fixed a bug in the export options window that caused column headings to be exported in the wrong order in certain rare scenarios Tab...
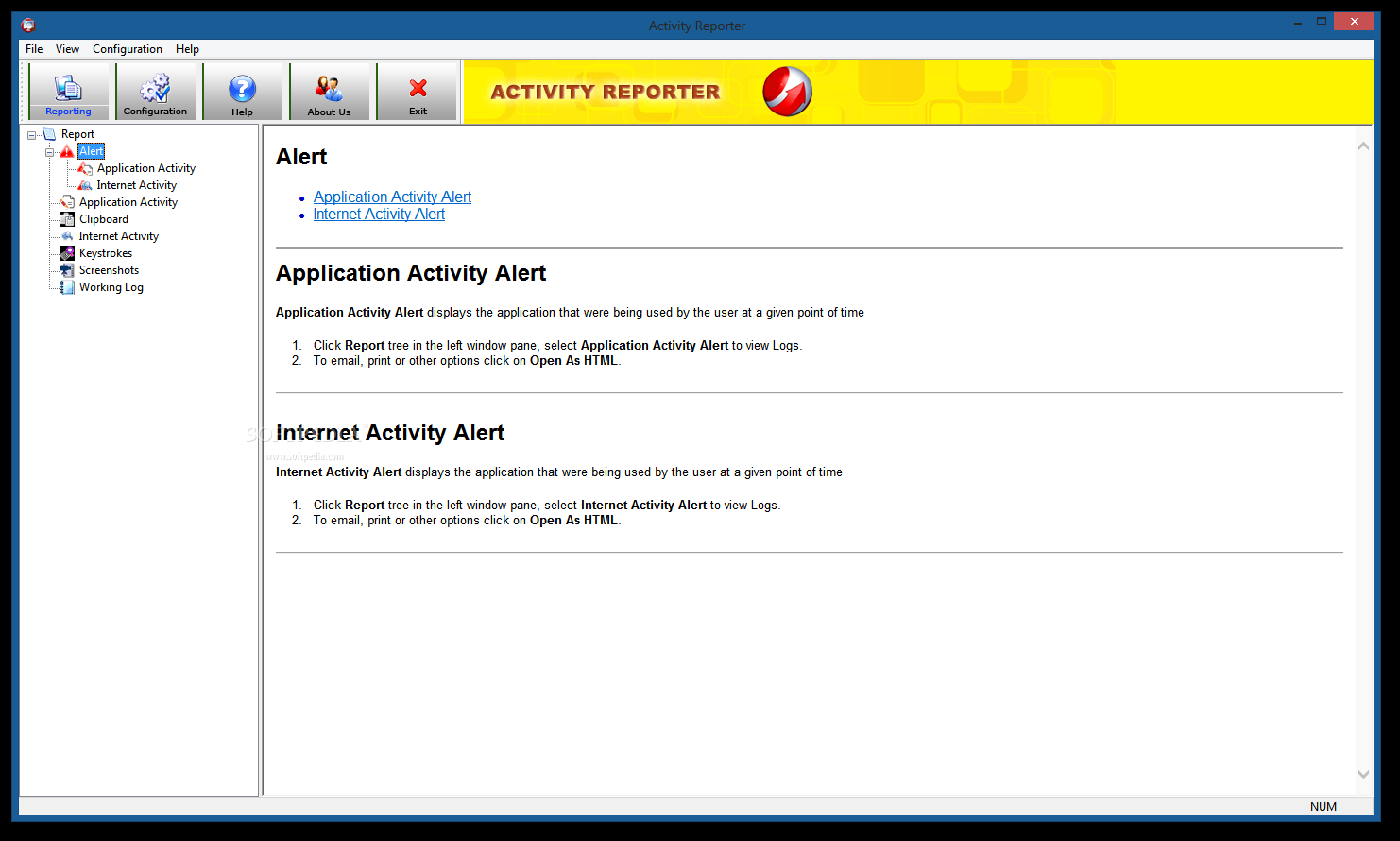
Activity Reporter
Keep an eye on all offline or online activities performed on your computer by all other users, with thorough configuration options, and options to export reports, or receive them by emailSure enough working with an active Internet connection makes...

Protegent 360
Keep your laptop safe and secure by protecting it against malware, trojans and viruses, monitor Internet activity and unformat corrupted drivesProtegent 360 is a security suite that packs several tools designed to keep an eye out for suspicious activity,...