Intel Identity Protection Technology Alternatives for Windows

Do you want to find the best Intel Identity Protection Technology alternatives for Windows? We have listed 38 Security that are similar to Intel Identity Protection Technology. Pick one from this list to be your new Intel Identity Protection Technology app on your computers. These apps are ranked by their popularity, so you can use any of the top alternatives to Intel Identity Protection Technology on your computers.
Top 38 Software Like Intel Identity Protection Technology - Best Picks for 2026
The best free and paid Intel Identity Protection Technology alternatives for windows according to actual users and industry experts. Choose one from 38 similar apps like Intel Identity Protection Technology 2026.
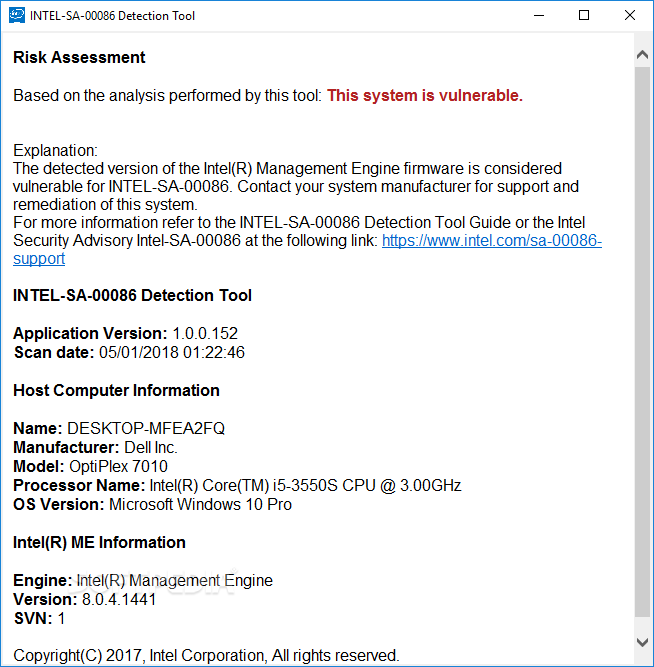
Intel-SA-00086 Detection Tool
A scanning tool specifically designed by Intel to detect whether your system uses one of the firmware versions exposed to the Intel-SA-00086 vulnerabilityFollowing a series of security-related issues reported by outside analysts, Intel conducted a security review of its...
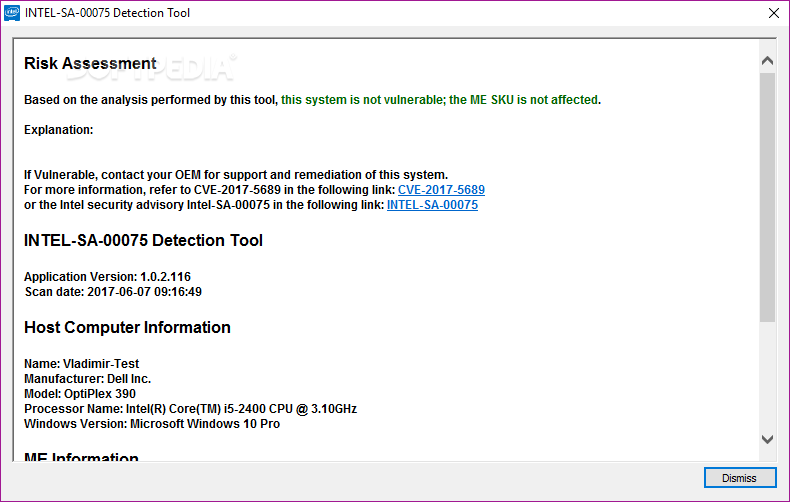
INTEL-SA-00075 Detection and Migration Tool
Bespoke utility developed by Intel to help you determine if your computer has been affected by the INTEL-SA-00075 chip vulnerabilityIf you like to stay up to date with the latest computer security news and events, you may know that...

McAfee True Key
Log in your account on multiple websites or services without typing your credentials every time by turning to this handy applicationIf you are regularly using several services that require authentication, you probably considered searching for a tool that can...
Ashampoo Spectre Meltdown CPU Checker
Check whether your computer is vulnerable against the Meltdown and Spectre security flaws Intel reported and get advice on the actions to takeThe most important security-related news that reached the headlines at the beginning of 2018 was related to...
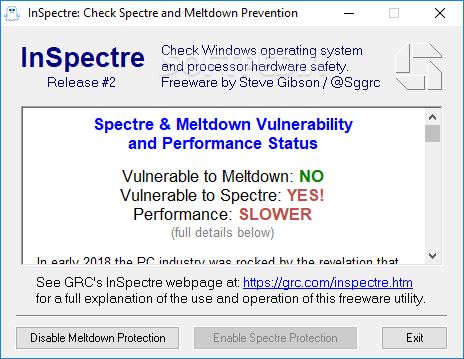
InSpectre
Find out whether your system is currently vulnerable to Spectre and Meltdown attacks in just one click using this straightforward app What's new in InSpectre release 8: Now shows whether an Intel microcode patch is (ever) available for Spectre:...
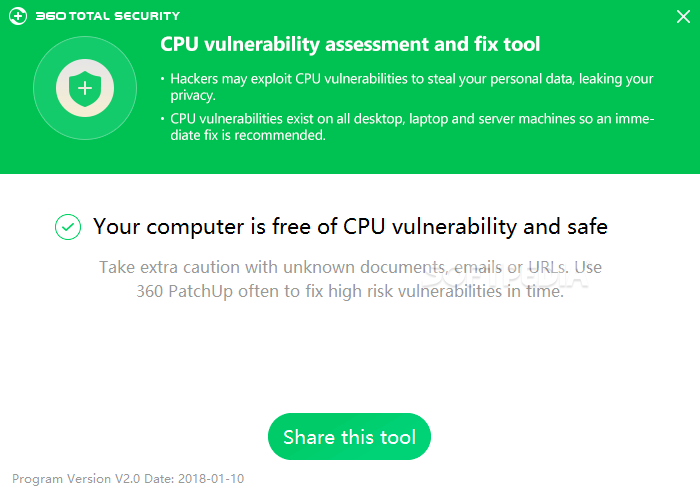
CPU Vulnerability Assessment and Fix Tool
A security tool designed to analyze your PC and discover whether any CPU vulnerabilities exist on your machine, be it a desktop or a serverGoogle's security team revealed important flaws in Intel CPUs in January 2018. Known as Meltdown...

Trustix Enterprise Firewall
Total Security Software for Enterprise Networks What's new in Trustix Enterprise Firewall 4.8.1: High Availability - False Failover Avoidance & Rich improved GUI Intrusion Detection System (IDS) - Ease of use for configuring from the Client VPN - Advanced...
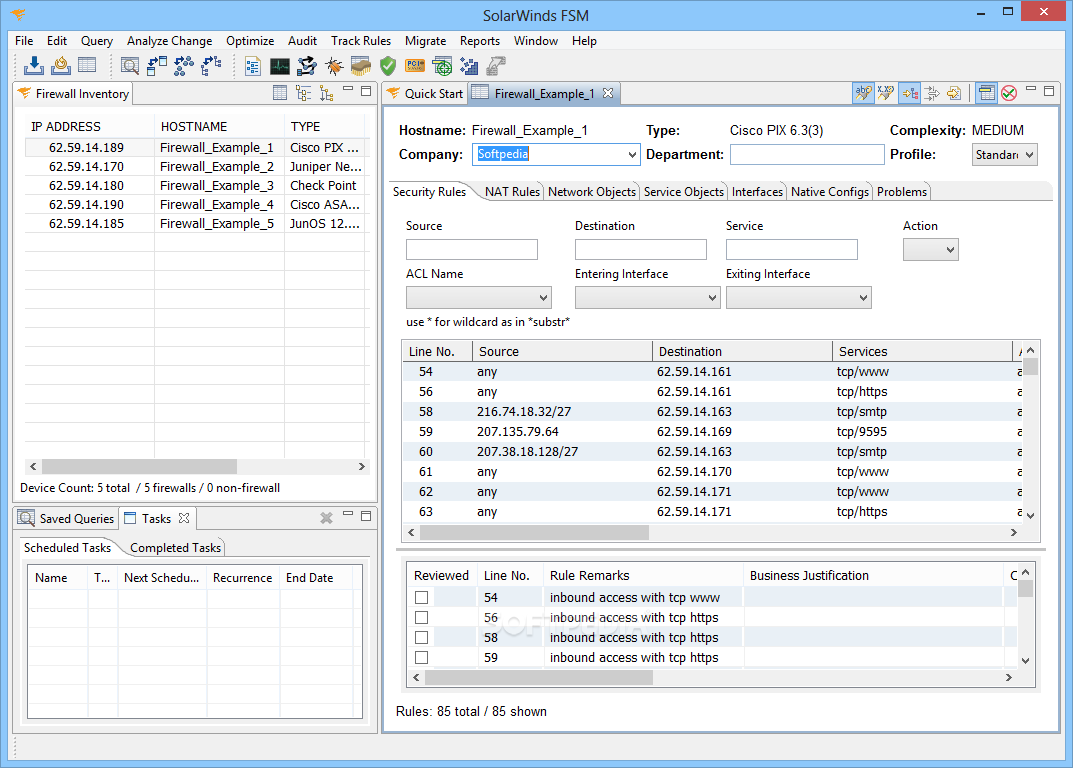
SolarWinds FSM (formerly Athena FirePac)
Automates security audits, deploys each firewall configuration, scans your inventory for high-risk firewalls and assess your risk profile in minutes What's new in SolarWinds FSM (formerly Athena FirePac) 6.6.5 Build 6.6.5-115-20141020: View firewall inventory and configuration details in the...
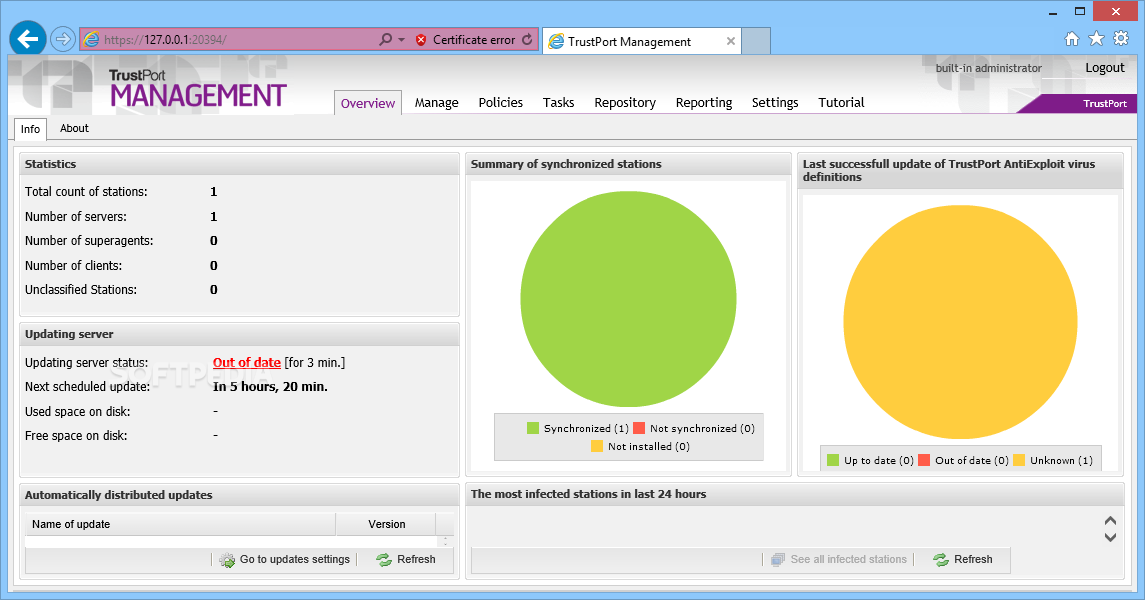
TrustPort Management
You can remotely control the functionality and events of anti-virus programs on the client computers in a network, from a centralized stationTrustPort Management is a reliable tool designed to help you handle the security on your local network, using...
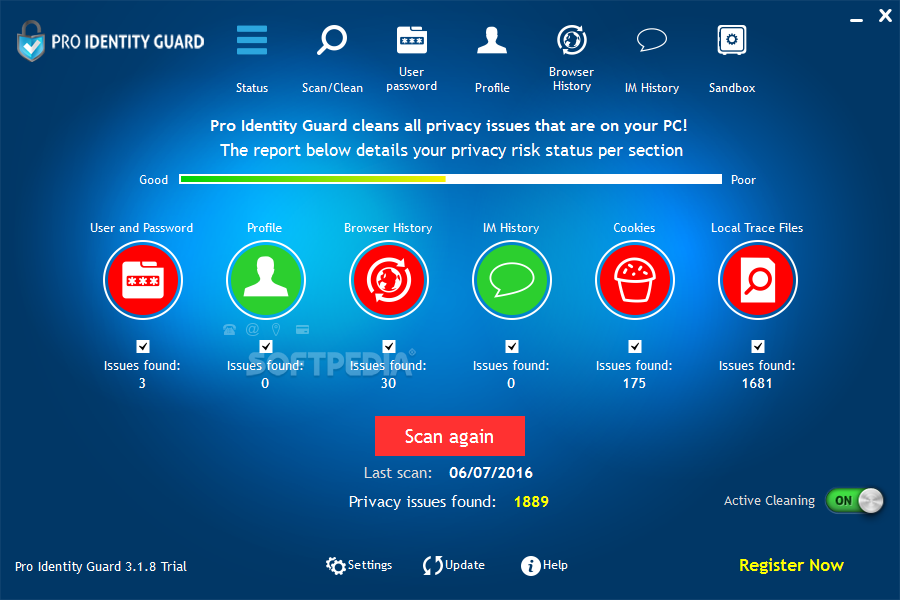
Pro Identity Guard
Find private information stored on your PC and delete if before it can be used for malicious purposes, with this easy-to-use applicationInformation about your accounts, activities and browsing history is stored on your computer by various applications, making you...
Norton Identity Safe
Powerful, reliable and accessible password management tool that makes logging into your favorite websites easier and more secure IMPORTANT NOTICEThere are numerous types of online content you need to protect while browsing the web, so remembering your passwords...
Identity Theft Preventer
Clean traces you leave online referring to sensitive and high-risk personal information such as login credentials and cookies thanks to this applicationNot a day goes by without you taking a ride on the information superhighway. However, it’s not really...
Maxilock Identity Safe
Maxilock Identity Safe is a pro-active 'real time' identity protection system which secures and safeguards your identityMaxilock Identity Safe is a pro-active 'real time' identity protection system which secures and safeguards your identity by delivering additional layers of protection...
Identity Cloaker
A lightweight and efficient application that aims to offer you the ability to secure your Internet privacy through anonymity protection servicesIdentity Cloaker is a user-friendly and intuitive piece of software whose main purpose is to offer you the proper...
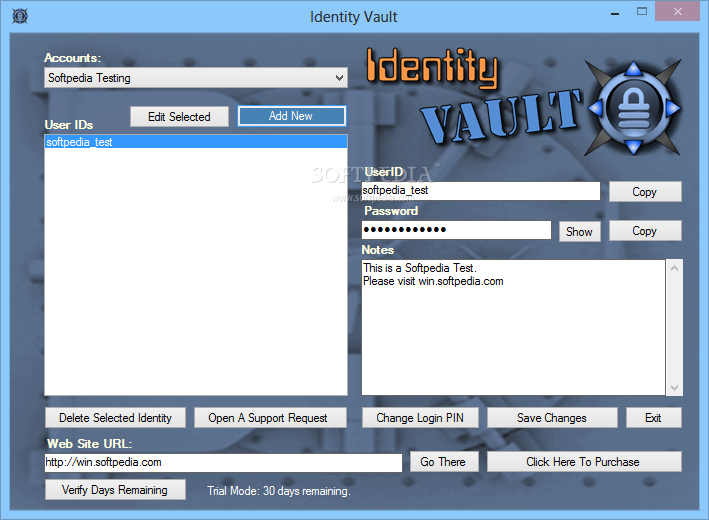
Identity Vault
A practical and secure solution specially designed for users who need to store IDs, passwords and personal information on their computerIdentity Vault is a reliable and effective software solution that comes in handy for users who need to manage...
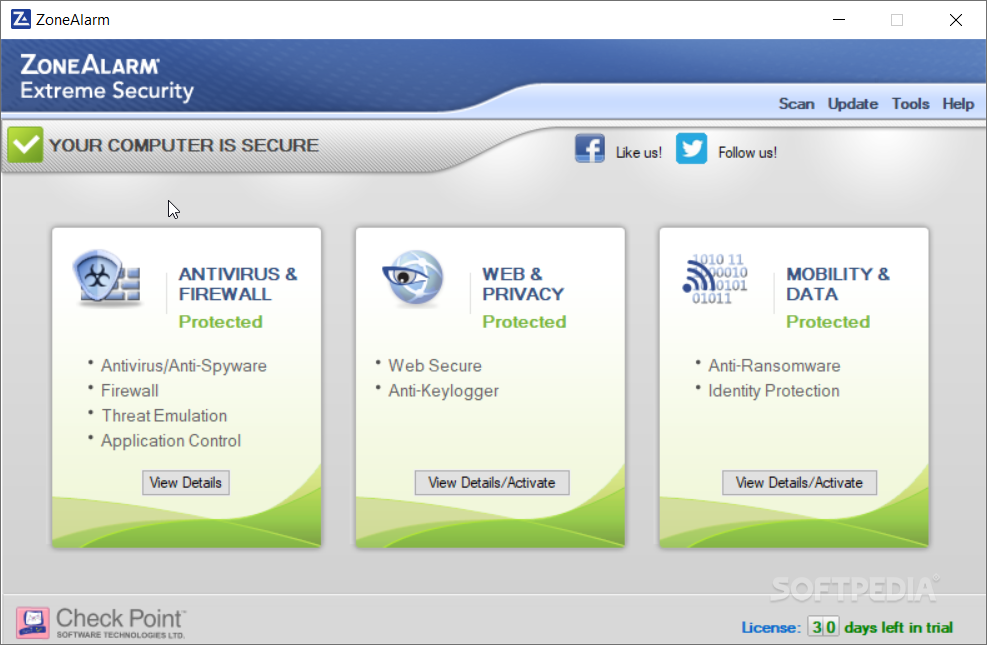
ZoneAlarm Extreme Security
Includes everything in ZoneAlarm Security Suite and integrates the comprehensive Web security features of ZoneAlarm ForceField, adding an extra security layer to your computer IMPORTANT NOTICE What's new in ZoneAlarm Extreme Security 15.8.043.18324: Improved: Stability, Security Fixed: Bug...
CompuSec PC Security Suite
A security software designed to protect desktops and notebooks What's new in CompuSec PC Security Suite 5.3.0: Support for Windows 7 (32 & 64 bit), Windows Server 2008 & Server 2008 R2 New and improved DataCrypt for container...
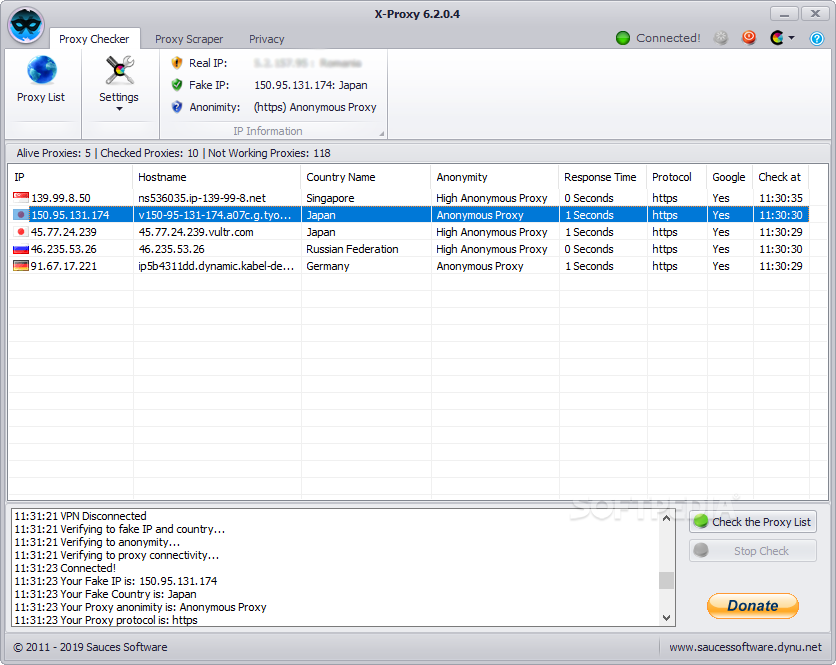
X-Proxy
Surf the Internet anonymously, change your IP address, prevent identity theft and intrusion from hackers by using a proxy IP server What's new in X-Proxy 6.2.0.4: Removed Hijacker Homepage Scan. Removed vpn servers. Updated the code for the new...
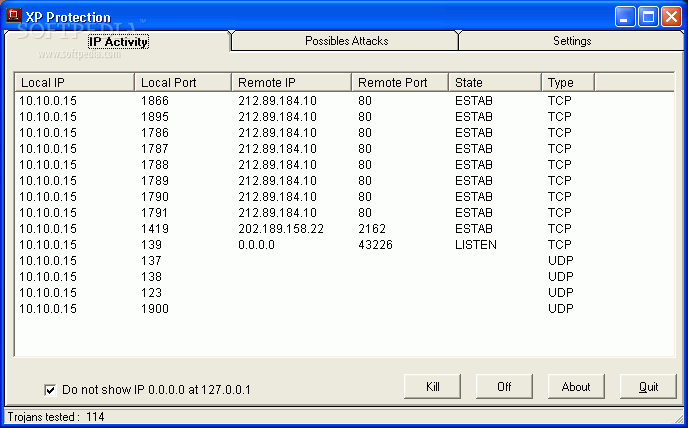
XP Protection
XPProtection provides instant online security in a user-friendly interfaceXPProtection provides security in a user-friendly interface, making you aware of any attacks from hackers, and Trojans.New features include protocol driver level protection, enhanced logging, user selected scan delay, kill on...
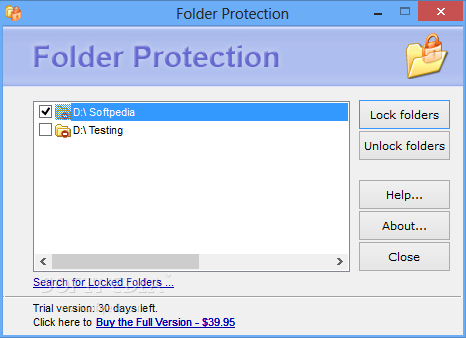
Folder Protection
Prevent access to folders storing sensitive information by easily locking them up with a password straight from their context menuFolder Protection has been created as a simple and uncomplicated solution, thus targeting all types of users that want to...
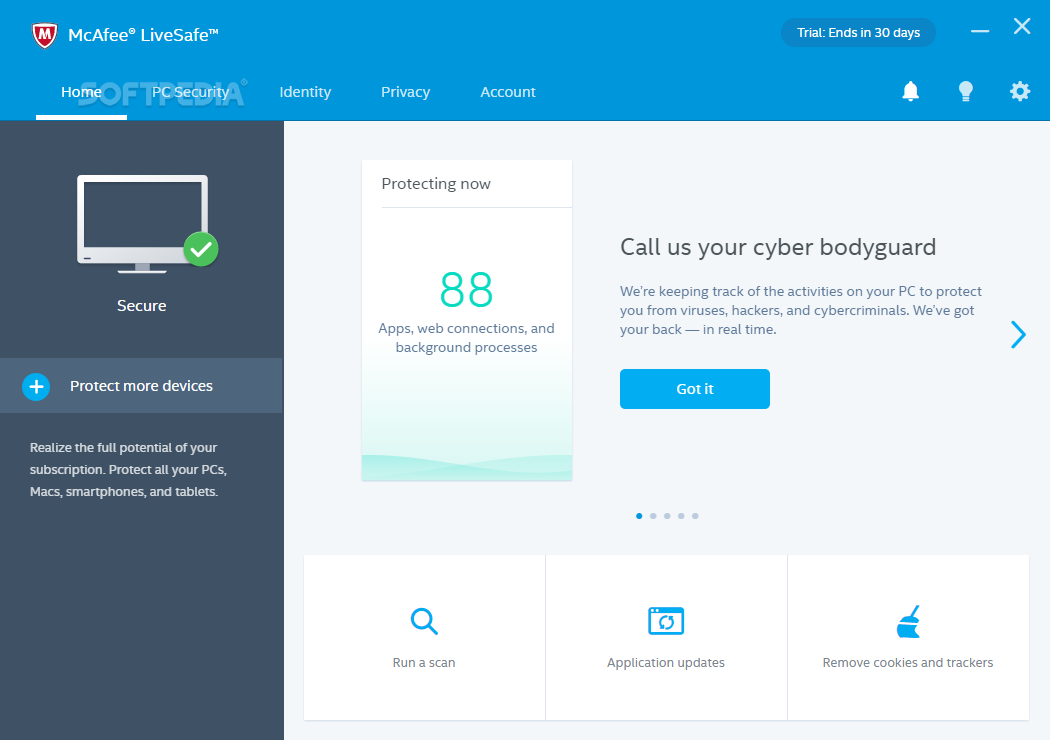
McAfee Total Protection
An effective protection solution against virus, online and network threats, which also features anti-spam and firewall componentsKeeping malware infections at bay by installing a fully-featured antivirus solution on your computer might not prove to be enough to keep your...
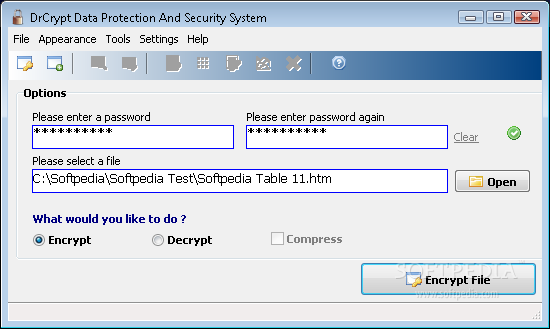
DrCrypt Data Protection and Security System
Secure your files and folders with strong password encryptionDrCrypt, is based our brand-new encryption system which is designed to be fast, reliable and stable. The main difference of DrCrypt from all those similar solutions; fastness and low system resource...
Cyberoam EndPoint Data Protection Suite
Protect your Data. Protect your AssetsCyberoam Endpoint Data Protection protects the organization's endpoints from data leakage through Identity and group-based policy controls, encryption, shadow copies, logging, reporting and archiving. Cyberoam offers data protection and asset management in four easy-to-deploy...
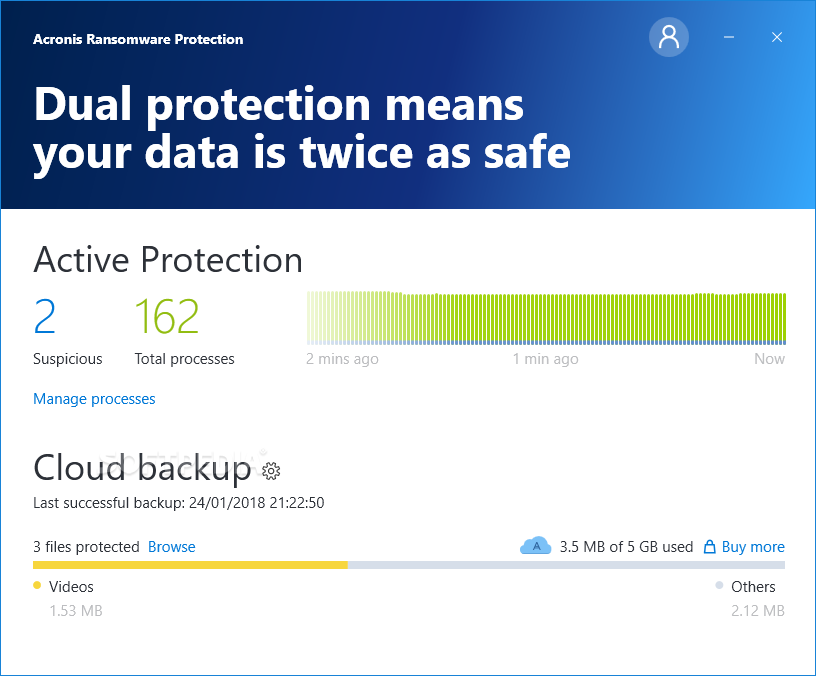
Acronis Ransomware Protection
Monitors active processes on your computer and identifies suspicious ones, allowing you to create whitelists and blacklists to trust or block certain processes What's new in Acronis Ransomware Protection Build 1700: What's new: Issue fixes and other improvements Known...
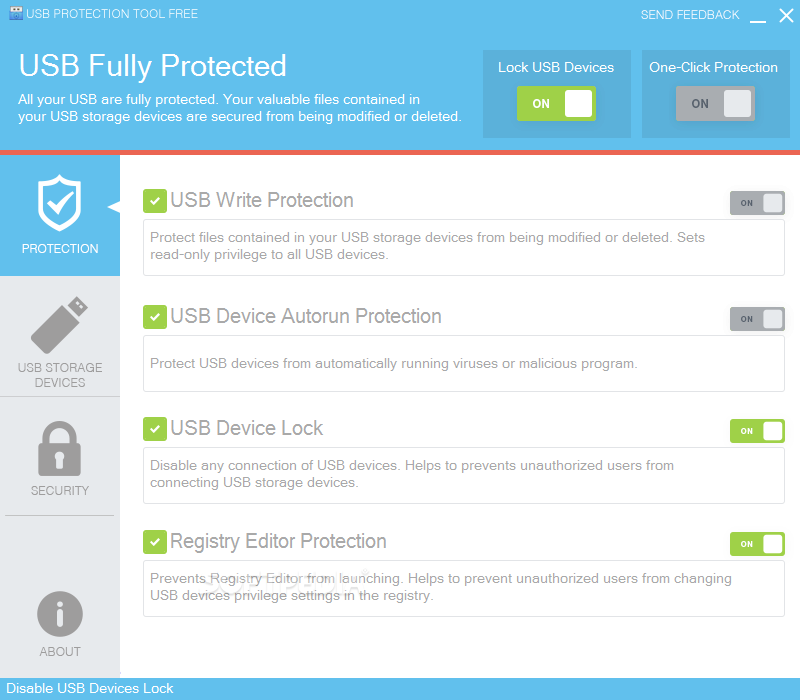
USB Protection Tool
Secure your USB sticks by instituting write and autorun protective measures with this intuitive application that can be password-protected What's new in USB Protection Tool 1.0: Updated: Bugs on Windows 8 Updated: Bugs when reloading drives Added: Password Protection...
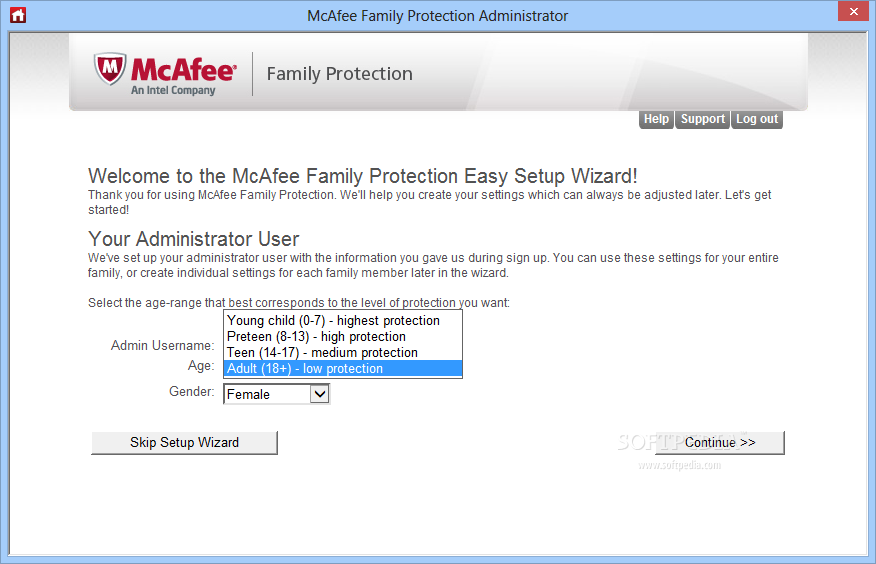
McAfee Family Protection
Allows parents to set a collection of rules for preventing exposure to inappropriate content, monitoring the time that children spend onlineMcAfee Family Protection is a promoter of child safety inside the web environment, delivering a set of rules that...
Forefront Endpoint Protection Tools
Use Group Policy for centralized managementThese tools make it easier for Forefront Endpoint Protection 2010 customers to use Group Policy for centralized management, provide optimized settings for various server roles, and diagnose and troubleshoot support issues.FEP Group Policy Tools...
USB Virus Protection
Ensure that autorun.ini viruses commonly found in Flash sticks do not find their way into your computer using this simple and straightforward toolWithout denying the Flash memory sticks can come in handy in numerous occasions, sometimes they can become...
M2SYS-Biometrics Suite
M2SYS-Biometrics Suite - dynamic and robust M2SYS fingerprint scanning/recognition moduleM2SYS-Biometrics Suite is created to secure PCs utilizing the dynamic and robust M2SYS fingerprint scanning/recognition module.Here are some key features of "M2SYS Biometrics Suite":· secure pc login · password management...
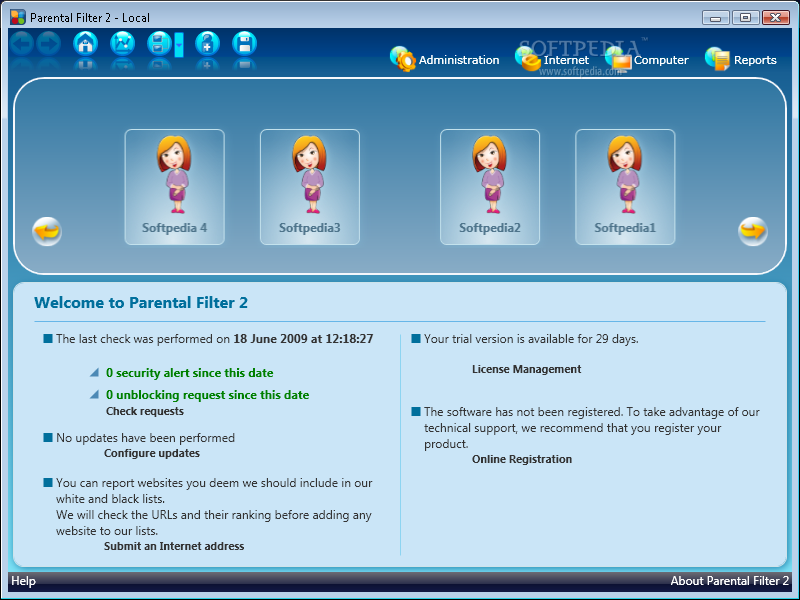
Profil Parental Filter
The best of the Internet for all the family! What's new in Profil Parental Filter 2: It’s now quick and easy to create a profile for each of your children by choosing among predefined models (child, preteen, teenager, young...

Microsoft Security Assessment Tool
Provides information and recommendations about best practices for security within an information technology (IT) infrastructure.The Microsoft Security Assessment Tool (MSAT) was designed to be a risk-assessment application that provides information and recommendations about best practices for security within an...
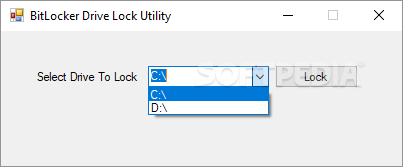
BitLocker Drive Lock Utility
Turn to this straightforward software utility in order to lock BitLocker-enabled drives at a mouse click and without the need to reboot your machineWhile encrypting individual files deters some unscrupulous individuals, the problem with this method is that it...
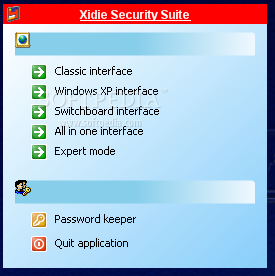
Xidie Security Suite
A complete security application especially designed for Windows.Xidie it's a complete security application combining a large variety of features.By combining cryptography with steganography, by using strong compression algorithms, well recognized and new encryption algorithms, classic and new steganographic techniques,...
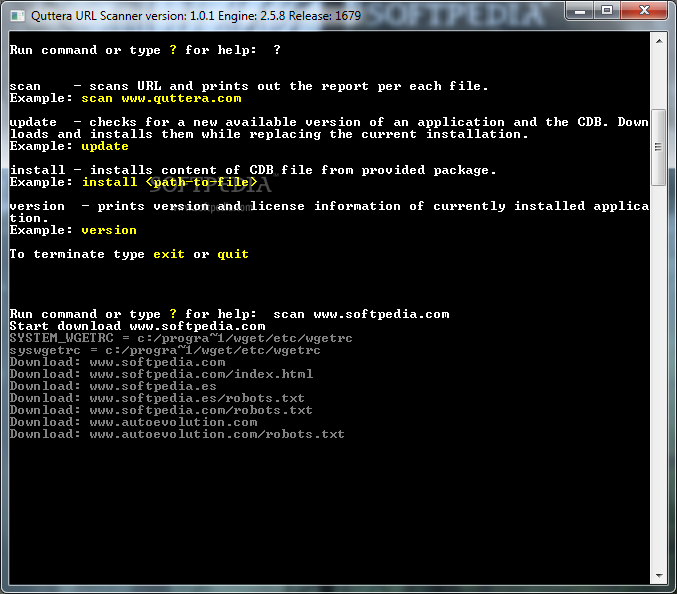
Quttera URL Scanner
Used for recognition and detection of web malware.Quttera URL Scanner is a standalone application that can investigate any website's content and verify if it is safe to browse.Quttera URL Scanner utilizes patent-pending heuristic and non-signature based web threats detection...
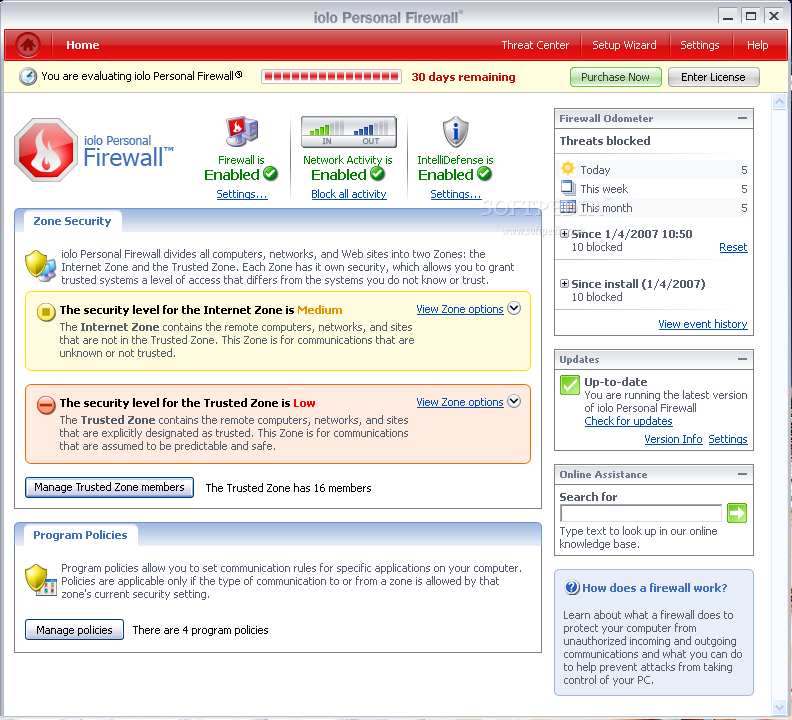
iolo Personal Firewall
A very useful firewall that blocks unwanted communication to and from your PCiolo Personal Firewall is a useful tool that blocks all unwanted communication to and from your PC, keeping your private information safe from hackers, cyber-criminals, and identity...
PC Activity Monitor Pro
This software utility captures all users activity on the PCPC Activity Monitor Pro is an ultimate invisible and undetectable easy-to-use monitoring and surveillance tool for both networked and individual PCs. It is professional software that captures all users activity...
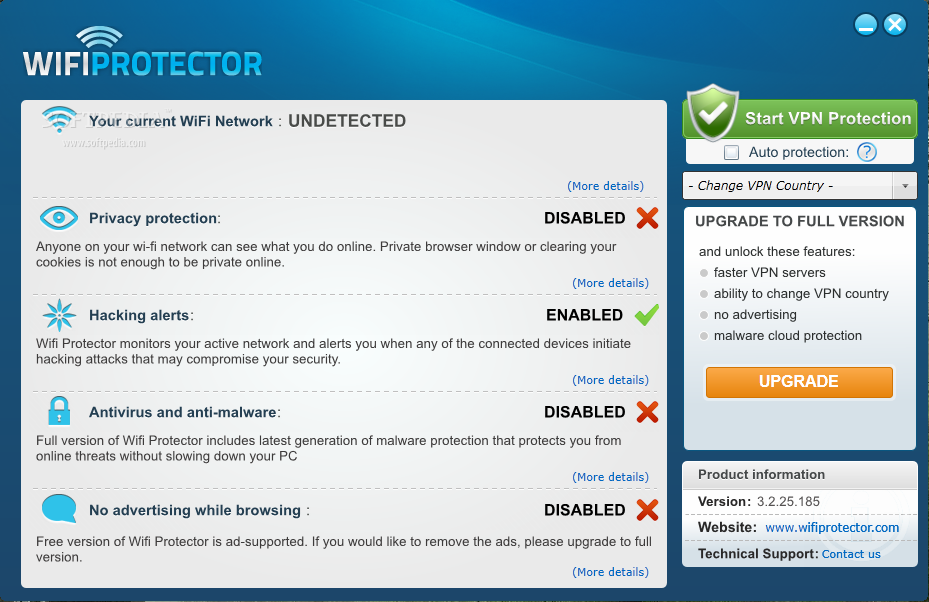
Wifi Protector
Makes sure that your WiFi network is secure with the aid of many different modules that identify threats and conceal your IP addressWifi Protector is a Wi-Fi hotspot shield, delivering groundbreaking protection for your wireless connection by detecting intruders...