Java Card Information Flow Verifier (JCSI) Alternatives for Windows
Do you want to find the best Java Card Information Flow Verifier (JCSI) alternatives for Windows? We have listed 45 Security that are similar to Java Card Information Flow Verifier (JCSI). Pick one from this list to be your new Java Card Information Flow Verifier (JCSI) app on your computers. These apps are ranked by their popularity, so you can use any of the top alternatives to Java Card Information Flow Verifier (JCSI) on your computers.
Top 45 Software Like Java Card Information Flow Verifier (JCSI) - Best Picks for 2025
The best free and paid Java Card Information Flow Verifier (JCSI) alternatives for windows according to actual users and industry experts. Choose one from 45 similar apps like Java Card Information Flow Verifier (JCSI) 2025.
Java Password Generator
Generate any number of passwords and set their complexity by including or excluding uppercase and lowercase letters, numbers, and symbolsJava Password Generator is a simple application you can use to create multiple passwords to protect your important documents, programs,...
Java Password Generator
Generate passwords using custom combinations of characters and symbols, specify number of items and length, and save all them to fileMost services which require subscription also ask for you to assign a password to your account, just so it...
Clear Java Cache
An easy way to clear you Java cacheClear Java Cache is developed as an easy-to-use and useful application that can automatically clear your Java cache folder.Now, you can use this simple, small and useful piece of software to keep...

Java Card Security for HP ProtectTools
A handy security solution for your HP notebookThis package contains the Java Card Security for HP ProtectTools for the supported notebook models and operating systems.The Java Card Security for HP ProtectTools provides an interface to manage Java Card security...
JavaSnoop
A tool that lets you intercept methods, alter data and otherwise test the security of Java applications on your computerNormally, without access to the original source code, testing the security of a Java client is unpredictable at best and...
Enfomi
Encrypt multiple files and folders using a password and various security algorithms, as well as create self-decrypting .jar archives using this Java toolEnfomi is a software application developed in Java, which gives you the possibility to encrypt files and...
HashTool
Calculate and compare checksums for files and text using this Java-based app with support for MD5, SHA256 and other algorithms, boost security by adding a cryptographic key (HMAC)Using Bouncy Castle Java cryptography API, HashTool is an application that can...
Personal Data Security (PDS)
Encrypt files, folders and notes using different security algorithms and by creating keystores and keys with this software applicationPersonal Data Security (PDS) is a software application developed in Java, which enables you to encrypt files and folders using passwords....
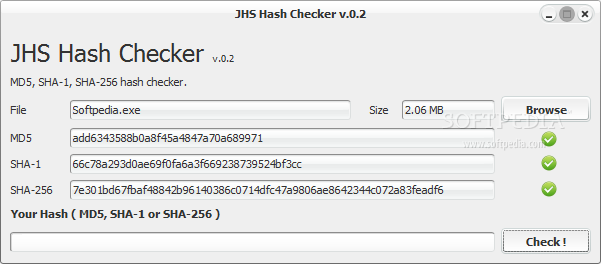
JHS Hash Checker
Calculate and compare the MD5, SHA-1 and SHA-256 signatures of files to check the content's integrity using this Java-based tool What's new in JHS Hash Checker 0.2: validation when the file empty threading generating hash value more responsive design...
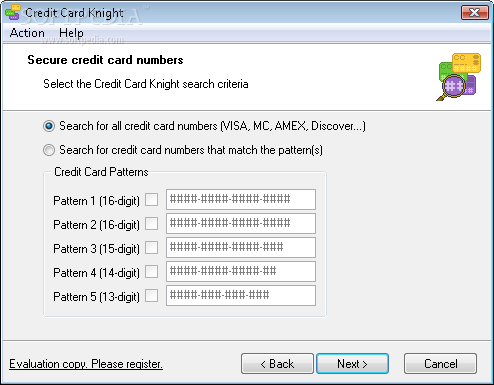
Credit Card Knight
Prevent your credit card data from stealing by carders from your computer What's new in Credit Card Knight 1.4: Minor bug fixed Read the full changelog Credit Card Knight prevents your credit card data from being stolen by...

HP Smart Card Security Module for ProtectTools
A useful application for enhancing the level of security on your HP notebookThe HP Smart Card Security Module for ProtectTools provides an interface to manage the Smart Card security features that are offered by HP.This package contains the HP...
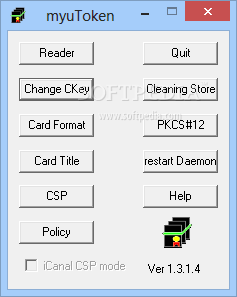
myuToken
This simple and user-friendly application aims to offer you an effective means of using your USB stick as a Smartcard, with several the security benefitsmyuTokenis a complex yet easy to handle piece of software that was developed to provide...
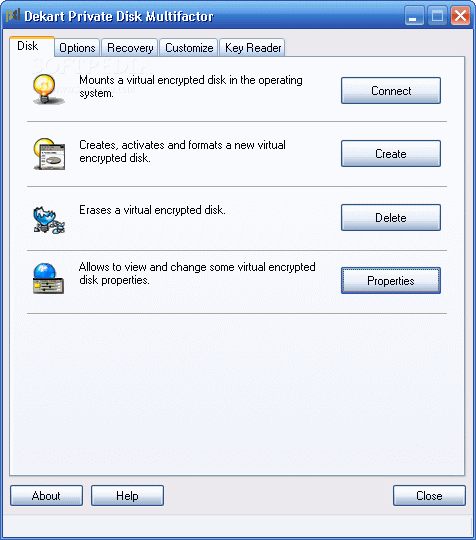
Dekart Private Disk Multifactor
Easy-to-use, secure and reliable disk encryption. Protect your private data What's new in Dekart Private Disk Multifactor 2.08: Now you can mount multiple disks at the same time, using different keys; The encryption program works with password-protected virtual disks,...
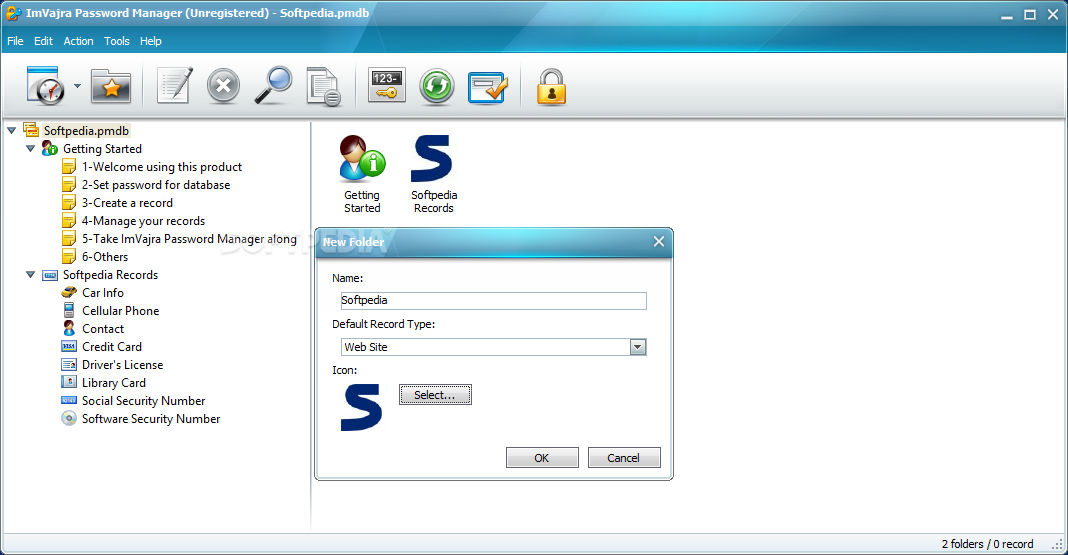
ImVajra Password Manager
Store, manage and edit passwords, account names, credit card numbers and other important and confidential data using this handy applicationThe Internet is filled with all sort of applications that you could use in order to manage data on your...
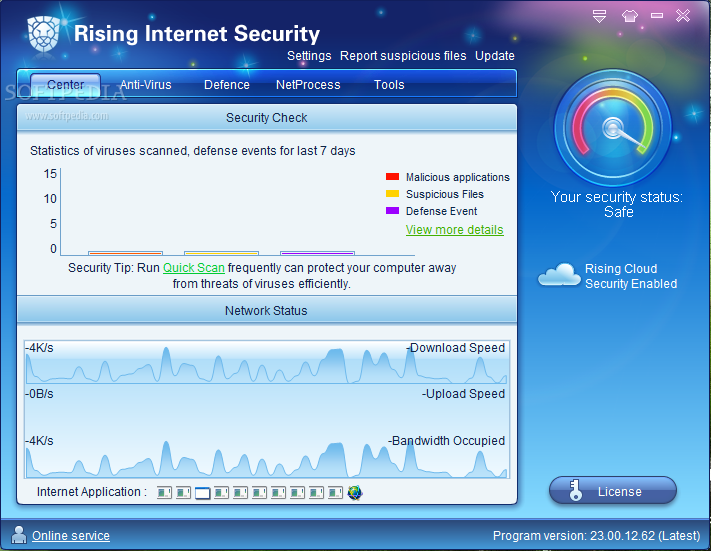
Rising Internet Security 2011
Provides extensive and continuous protection for your home and office computersRising Internet Security provides antivirus protection and customizable personal firewall service both, protects your computer against all types of Internet threats. Due to its Rising Cloud Security project, this...
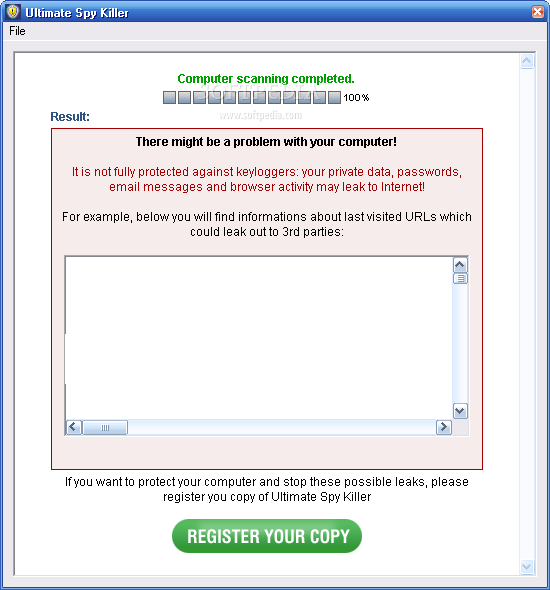
Ultimate Spy Killer
Ultimate Spy Killer is a program that kills Syware, Viruses and TrojansUltimate Spy Killer helps you detect harmful software such as Viruses, Adware ,Spyware, SpyBots, Worms, Trojan Horses, Hacker Tools and Keyloggers.The aim of Ultimate Spy Killer Pro is...
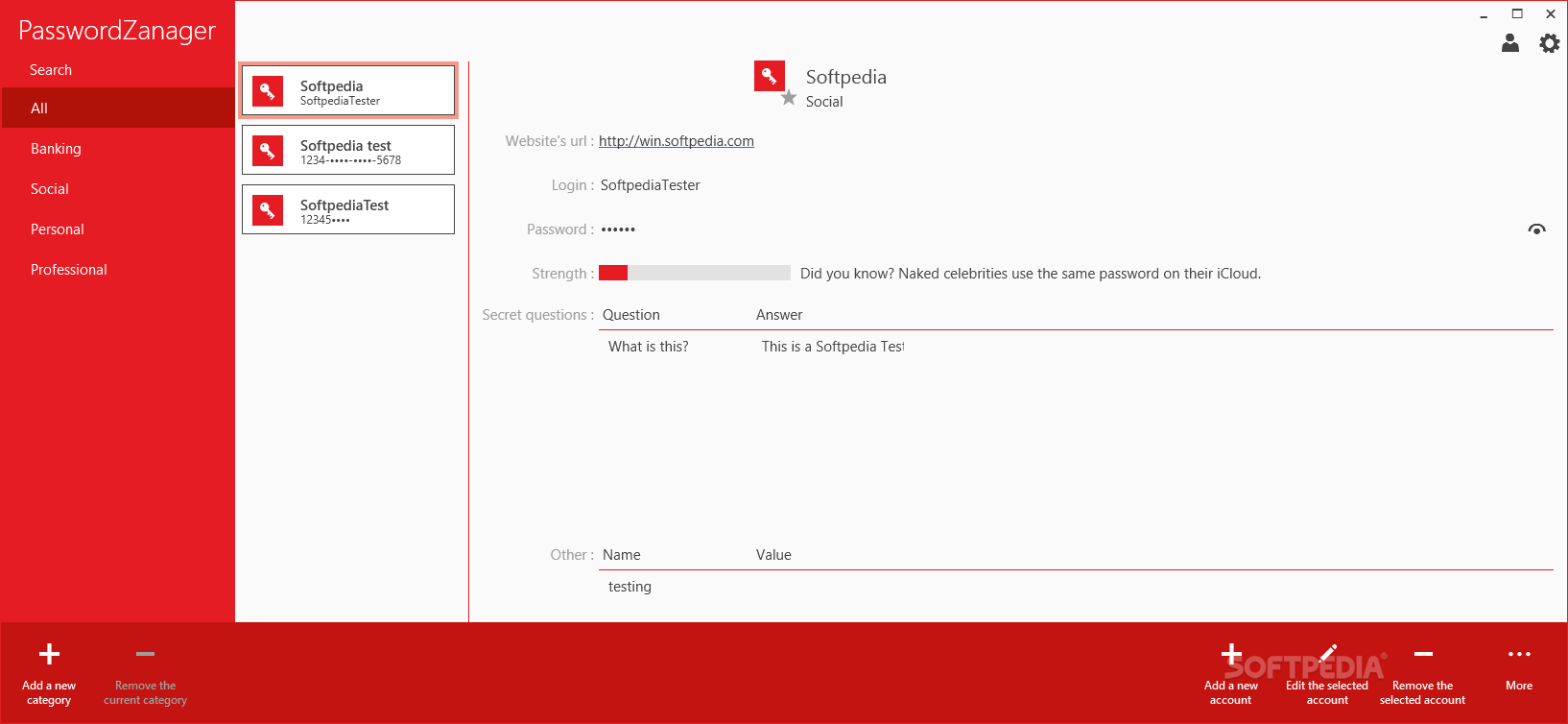
PasswordZanager
With this lightweight and efficient program, you can easily manage all your personal and professional passwords in a secure mannerPasswordZanagerwas developed as a method of helping you securely manage all your accounts’ information, serving a wide array of purpose,...
Windows Security Analyzer
A free tool that runs over 100 tests to gauge server securityWindows Security Analyzer is a handy application that will run over 100 tests in order to gauge server security against all best practices. Some tests include explanations and background information. It...

Microsoft Security Assessment Tool
Provides information and recommendations about best practices for security within an information technology (IT) infrastructure.The Microsoft Security Assessment Tool (MSAT) was designed to be a risk-assessment application that provides information and recommendations about best practices for security within an...
Ascendo DataVault
A complex and reliable password manager that ensures the protection of your personal information with the help of powerful AES encryption algorithmsAscendo DataVaultis a professional password security manager that safe keeps your private information be it passwords, PINs, usernames,...
1-abc.net Security Box
A small-sized and handy application suite consisting of several programs that help you protect your private information and data1-abc.net Security Box is a comprehensive tool for protecting private data and securing files. It integrates a password organizer, personal diary,...
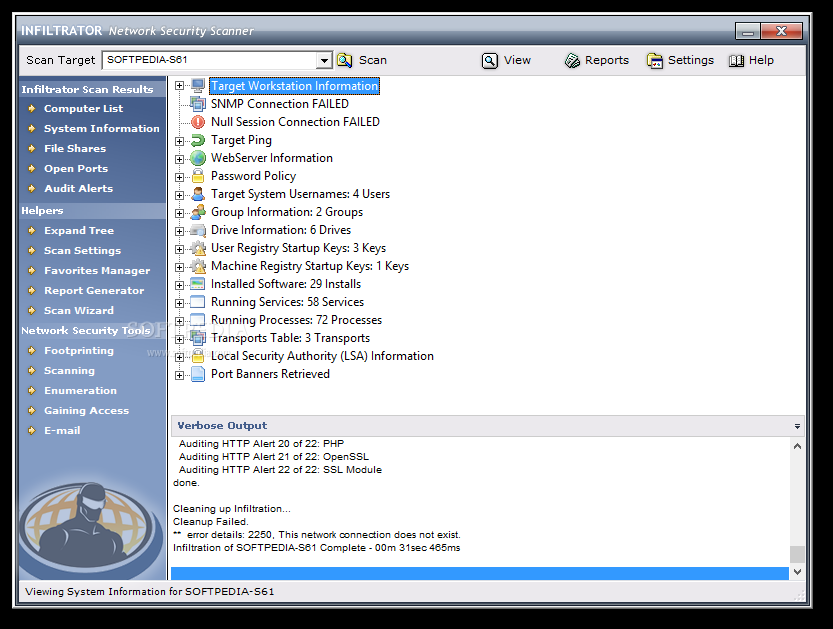
Infiltrator Network Security Scanner
A Network Security Scanning and Auditing SuiteInfiltrator Network Security Scanner can quickly audit your network computers for possible vulnerabilities, exploits, and information enumerations.It comes with a built-in database of known vulnerabilities, that can be updated online and allows you...

Maui Security Scanner
Maui Security Scanner allows you to scan for specific vulnerabilities, such as Fault Injection, SQL Injection and XSSMaui Security Scanner is an innovative security assessment software suite for today's sophisticated Web application environments..Maui Security Scanner ensures the security of...
Retina Network Security Scanner
A useful utility designed to identify system, application, database, OS and web application vulnerabilities via agent-based and/or agentless scanningRetina Network Security Scanner is a straightforward and reliable application that comes in handy for users who need to discover all...
Security System Analyzer
A tool designed to check your system for the latest security updates What's new in Security System Analyzer 1.6 Beta 2: Updated OVAL Security Check Plugin to support OVAL 5.4 schema Proxy support of NTLM authentication Reported Bugs fixed...
8Signs Firewall
protect a Windows Internet server, complete information and control over network security What's new in 8Signs Firewall 3.02: Fixed bug that could cause the firewall to crash if the user attempted to sort an IP Address Group Read...
Threat Analysis & Modeling
Threat modeling to empower application risk management. What's new in Threat Analysis & Modeling 3.0 Beta: Azure based CTL store Visio drawing surface for use cases Intelligent TFS Sync Automated tool update detection Read the full changelog The...
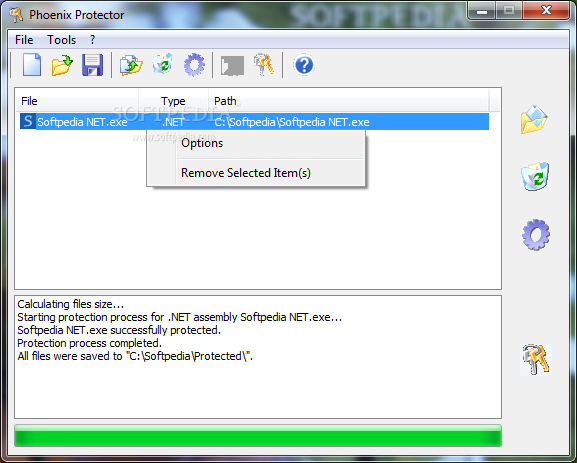
Phoenix Protector
A practical and reliable software intended for developers who need to secure their applications and .NET assemblies by making the code hard to interpretPhoenix Protector is a straightforward and effective piece of software especially designed for developers who need...
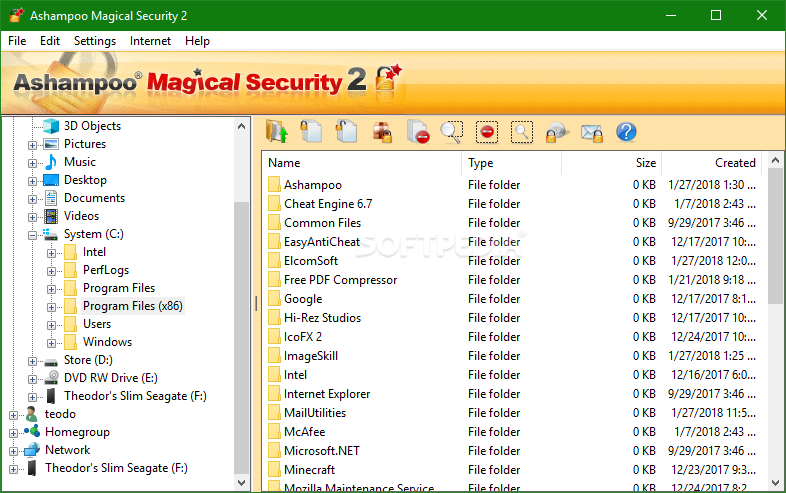
Ashampoo Magical Security
An intuitive application that helps users protect their sensitive data from unauthorized viewing by offering a powerful encryption algorithmKeeping your documents private from unauthorized viewing is a sensitive problem tackled by many dedicated tools on the market. While some...

Trustix Enterprise Firewall
Total Security Software for Enterprise Networks What's new in Trustix Enterprise Firewall 4.8.1: High Availability - False Failover Avoidance & Rich improved GUI Intrusion Detection System (IDS) - Ease of use for configuring from the Client VPN - Advanced...
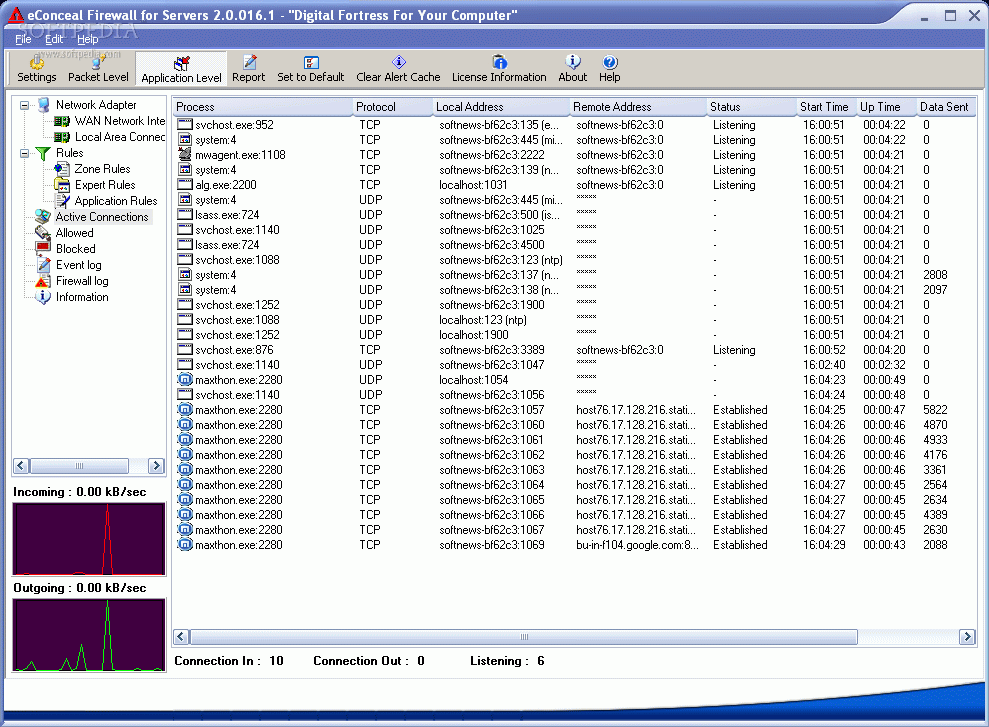
eConceal Firewall for Servers
eConceal is a powerful Firewall designed to protect your internal Network.eConceal is a powerful Firewall designed to protect your internal Network.eConceal Firewall for Servers is a powerful, highly advanced Gateway level Firewall designed to protect your internal Network against...
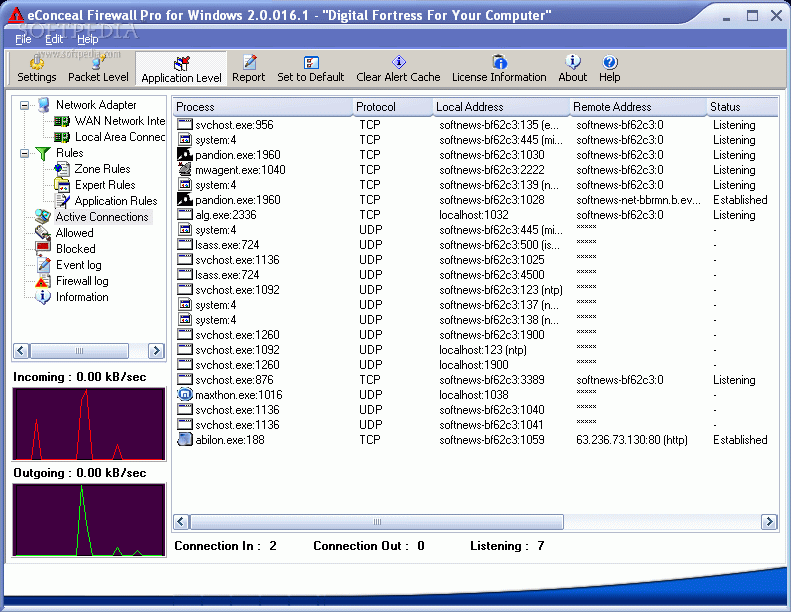
eConceal Firewall Pro for Windows
eConceal Pro for Windows is a powerful, highly advanced Network FirewalleConceal Pro for Windows is a powerful, highly advanced LAN Firewalldesigned to protect your PC against attacks via the Internet or Local Area Network.eConceal Pro offers customizable security with...

ip-shield
Browse the web while keeping your virtual identity secured by connecting through a VPN network with this straightforward application What's new in ip-shield 2.3 Build 4100: Country selection for Netherlands Read the full changelog Similarly to a city...
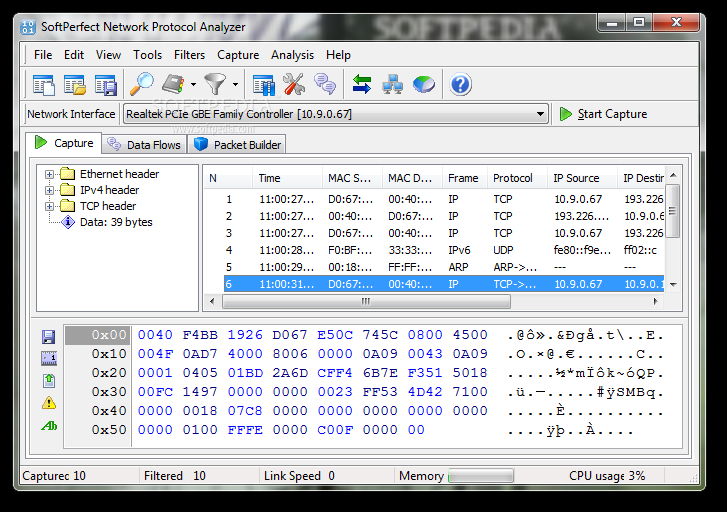
SoftPerfect Network Protocol Analyzer
A comprehensive and reliable network sniffer that helps network administrators to analyze and monitor networks and Internet connections What's new in SoftPerfect Network Protocol Analyzer 2.9.1: Added Windows high DPI awareness for high-resolution displays. Fixed sorting IP Senders and...
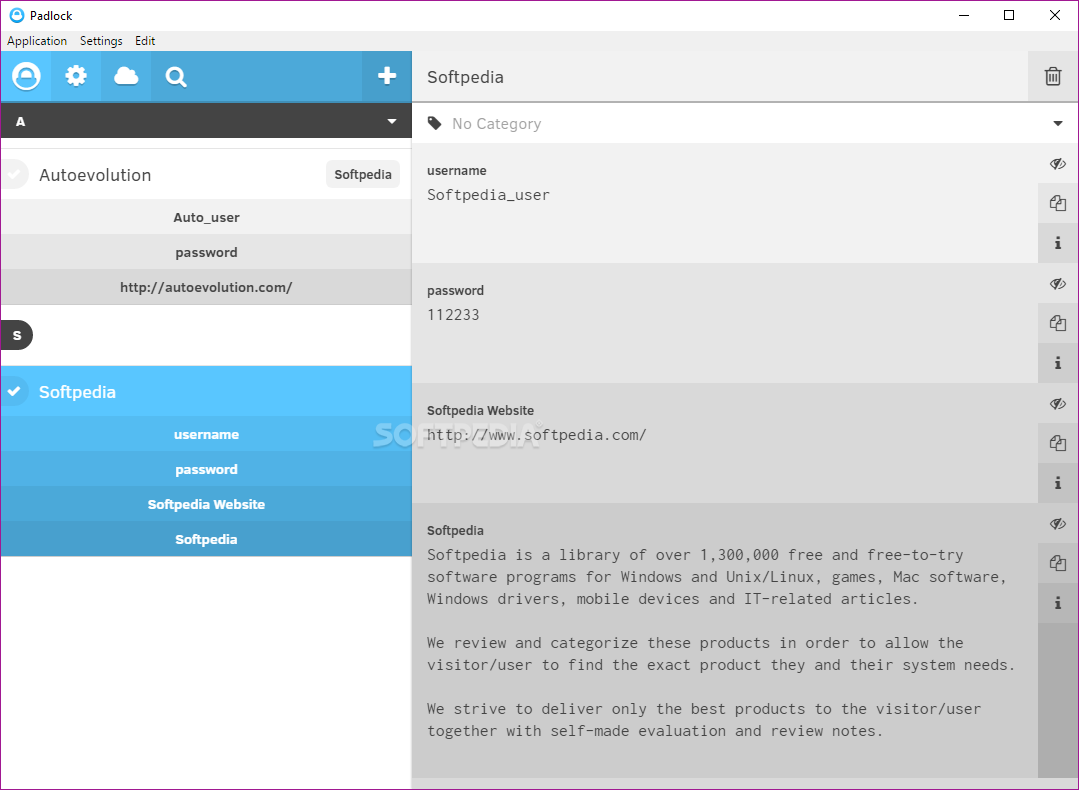
Padlock
Securely store all your sensitive information as well as passwords or other types of credentials by relying on this open-source password manager What's new in Padlock 3.1.0: Improved flow for creating a vault item If a vault filter is...
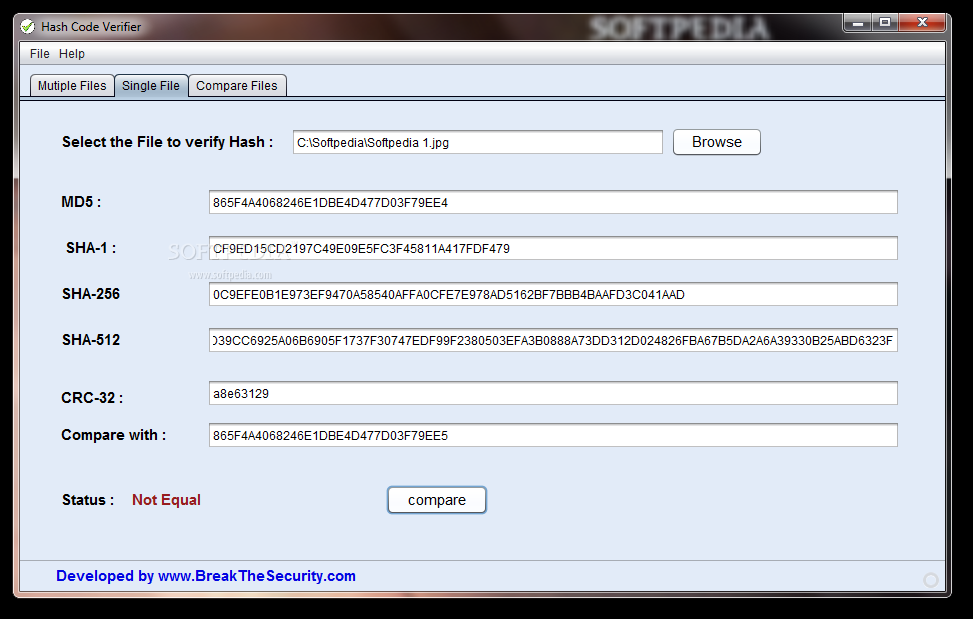
Hash Code Verifier
Calculate file hashes, namely MD5, SHA-1, SHA-256, SHA-512 and CRC-32, for multiple files at the same time, compare two files, and export the info to HTML or plain text file formatHash Code Verifier is a small software application whose...
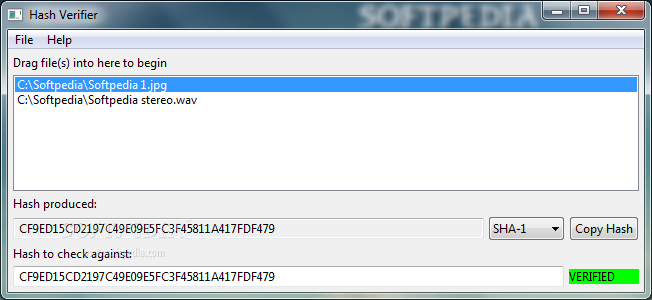
Hash Verifier
Qucickly calculate and compare the SHA1, SHA256, SHA384, SHA512, MD2 and MD5 checksums of your files to find out if they are identicalHash Verifier is a small-sized tool developed in Java, which is capable of calculating the SHA1, SHA256,...
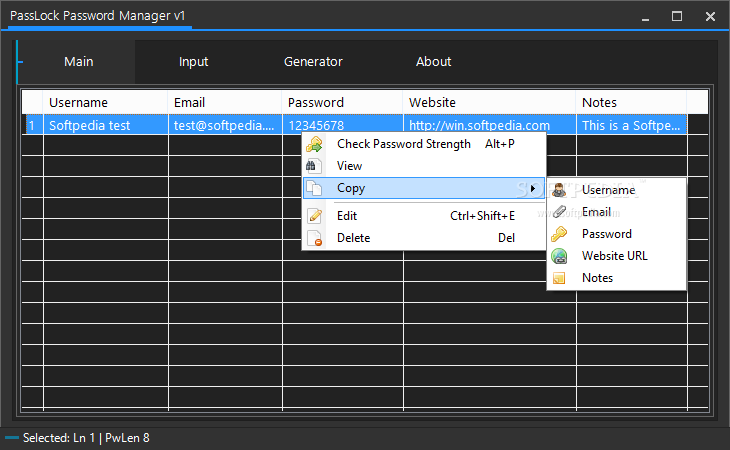
PassLock Password Manager
A reliable application that enables you to determine the strength of your passwords, store them in a database or generate new security codes What's new in PassLock Password Manager 1.7: Added autocomplete for Username, Email, and URL Added search...
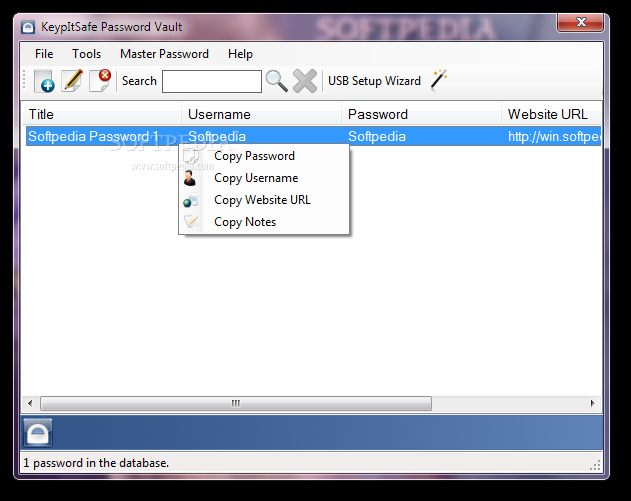
KeypItSafe Password Vault
Enables you to easily and safely store your website passwords within a secure application, as well as generate passwords and test their strengthThere are a significant number of websites that require a password to access properly, users can have...
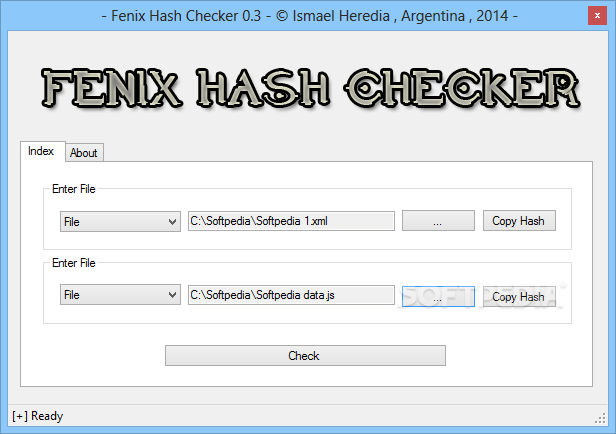
Fenix Hash Checker
A simple to use application dedicated to calculating the checksums of two files and compare them or analyzing the provided hashesFenix Hash Checkeris a reliable software that enables you to compare two files and determine whether they are identical...
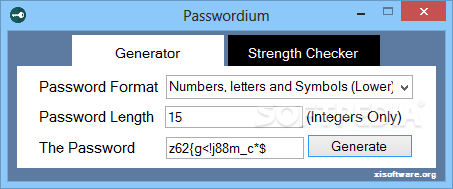
Passwordium
A simple to use application dedicated to generating passwords based on random selection of letters, numbers or symbols and with a specified lengthPasswordium is a lightweight, yet reliable program which allows you to generate powerful passwords for your online...
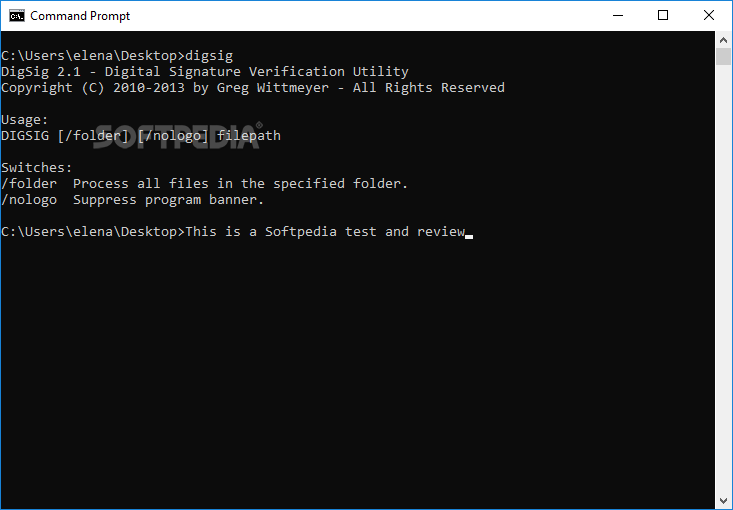
DigSig
Check the integrity of digital signatures within applications and other types of files, thanks to this simple and straightforward command-line toolIf you frequently worry about the authenticity of downloaded files and that someone might have tampered with the data,...
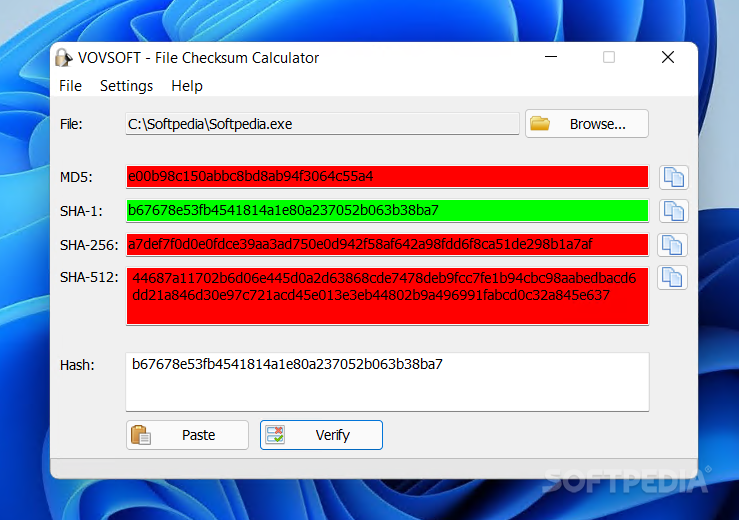
File Checksum Calculator
Calculate MD5, SHA-1 and SHA-256 file hashes, and them compare them to an available checksum to see if they match, with this simple utilityHash functions are commonly used to verify a file’s integrity and ensure it has not been...
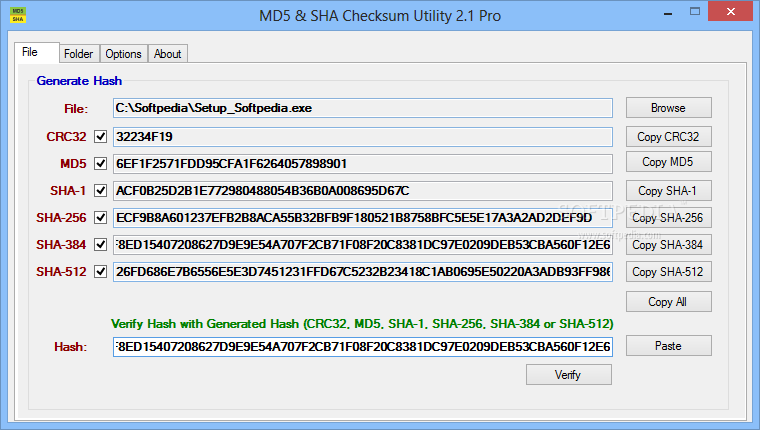
MD5 & SHA Checksum Utility Pro
A useful application that was especially created to offer users a simple means of having the hashes for their files calculated on the spotThe state of every file is dictated by a unique code, which can be interpreted under...