Windows Shortcut Exploit Protection Tool Alternatives for Windows

Do you want to find the best Windows Shortcut Exploit Protection Tool alternatives for Windows? We have listed 46 Security that are similar to Windows Shortcut Exploit Protection Tool. Pick one from this list to be your new Windows Shortcut Exploit Protection Tool app on your computers. These apps are ranked by their popularity, so you can use any of the top alternatives to Windows Shortcut Exploit Protection Tool on your computers.
Top 46 Software Like Windows Shortcut Exploit Protection Tool - Best Picks for 2025
The best free and paid Windows Shortcut Exploit Protection Tool alternatives for windows according to actual users and industry experts. Choose one from 46 similar apps like Windows Shortcut Exploit Protection Tool 2025.
Flash Windows Hider
Easily hide a custom selection of running windows, as well as desktop icons and the taskbar itself with the help of hotkeys thanks to this appYour desktop can only hold so many elements, and working with too many windows...
Windows Security Analyzer
A free tool that runs over 100 tests to gauge server securityWindows Security Analyzer is a handy application that will run over 100 tests in order to gauge server security against all best practices. Some tests include explanations and background information. It...
Windows XP Firewall Port & Application Manager
A simple, yet effective and reliable application aimed at protecting your computer and managing all the allowed programs and port numbersWindows XP Firewall Port & Application Manager is a practical and straightforward application worth having when you need to...
Windows Security Officer
Enforce security of your computer for multiple users or simply make your work more comfortable by managing Internet, desktop, system, accounts, files and folders, and more tweaksThere are a variety of default settings in Windows which allow you to...

CorreLog Windows Agent Package
Converts Windows event logs to syslogs.CorreLog Windows Agent Package is an application that will help support the IT security community.The application will add true syslog capability to any Windows platform. The software contains the Syslog Message Service, support utilities,...
Windows XP Security Console
Allows you to assign various restrictions to specific users, whether you're running XP Pro or XP HomeWhen you're outside of a domain environment, XP has some features missing. XP Home leaves you completely without the Group Policy Editor, while...
eConceal Firewall Pro for Windows
eConceal Pro for Windows is a powerful, highly advanced Network FirewalleConceal Pro for Windows is a powerful, highly advanced LAN Firewalldesigned to protect your PC against attacks via the Internet or Local Area Network.eConceal Pro offers customizable security with...
Caruban Security Windows
This application is designed to keep your computer safe from threat, by detecting and cleaning malicious files or system settingsCaruban Security Windowsis designed to protect your computer against malicious files stored on it or against Web threats. It can...
Windows Firewall Ports & Application Manager
Add exceptions to the Windows firewall by selecting executables of interest, or adding range of ports across LAN or WAN with this practical, portable appWindows takes some default security measures to keep all of your files protected. An important...
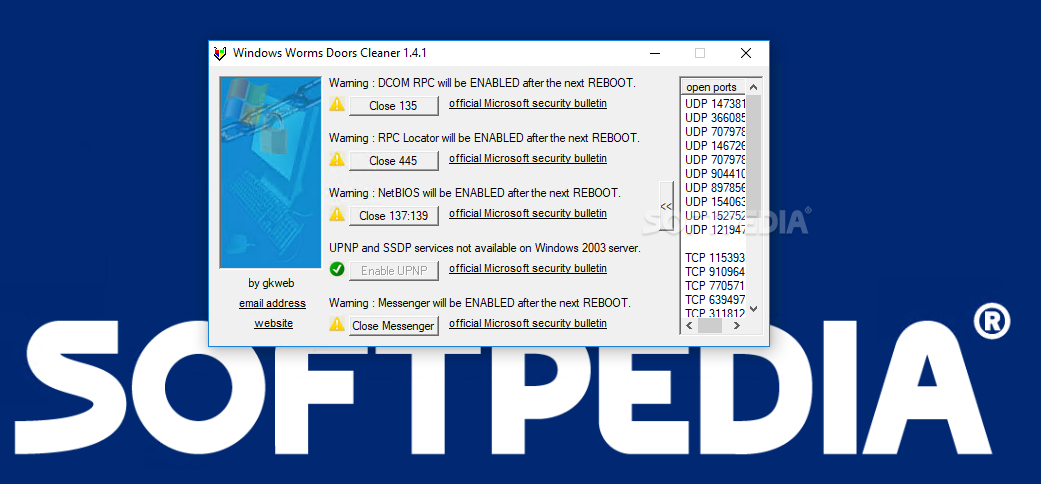
Windows Worms Doors Cleaner
Detects the enabled services by checking registry entries, the local open ports and the running services to prevent unauthorized access What's new in Windows Worms Doors Cleaner 1.4.1: website link on the GUI updated email link on the GUI...
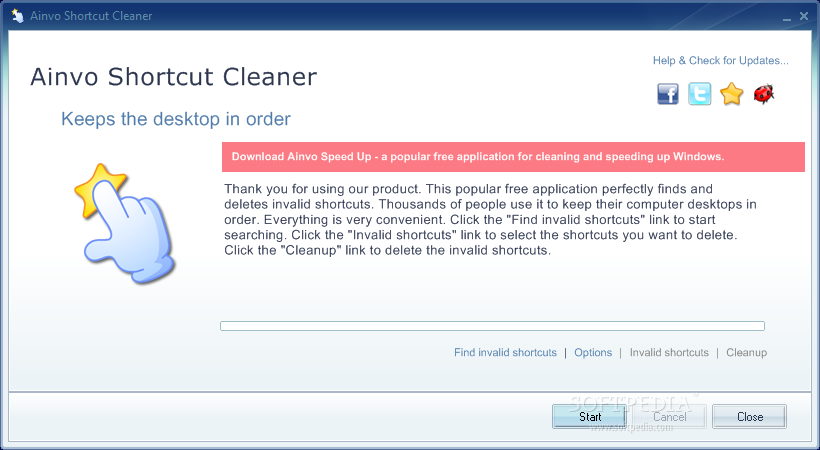
Ainvo Shortcut Cleaner
Find and remove invalid shortcuts that are no longer linked to valid applications, and analyze reports using this straightforward utility What's new in Ainvo Shortcut Cleaner 2.3.2.351: The program operation map has been added. Now it is possible to...
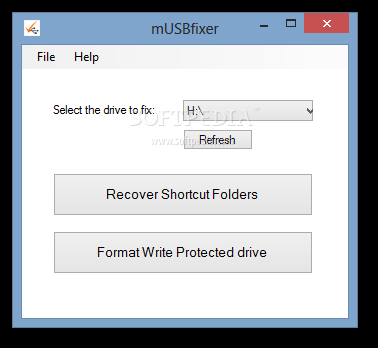
mUSBfixer
Format USB drives and SDs, and recover data by converting shortcut folders to actual directories that you can browse using this simple applicationmUSBfixer is a small software application specialized in formatting and repairing USB flash drives using a set...
Desktop USB Security Key
A new security tool for your USB thumb driveDesktop USB Security Key is a useful tool that installs to any USB thumb drive and adds extra security when the user is away from their PC or Laptop. Take out...
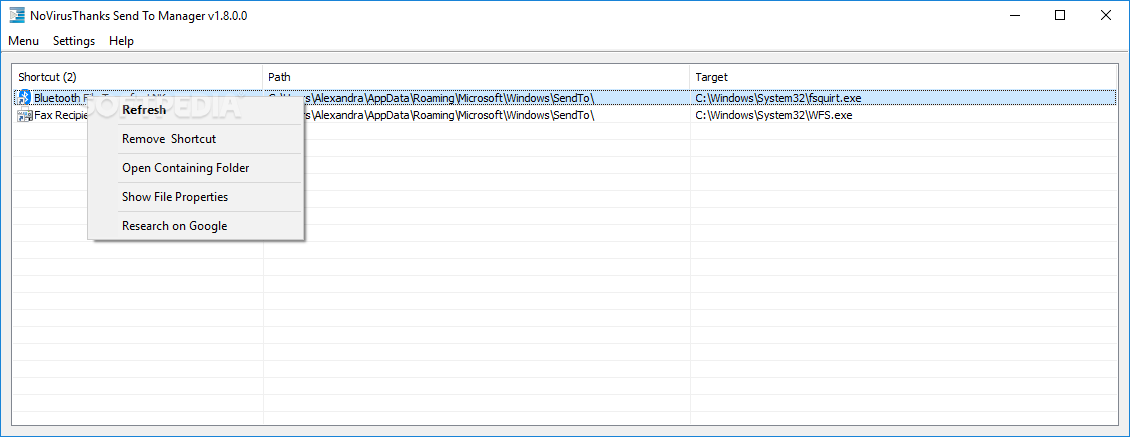
NoVirusThanks Send To Manager
Check out the file properties and remove unwanted shortcuts from your system or add new ones to the files you are using often via this tool What's new in NoVirusThanks Send To Manager 1.8: All .exe files are digitally...
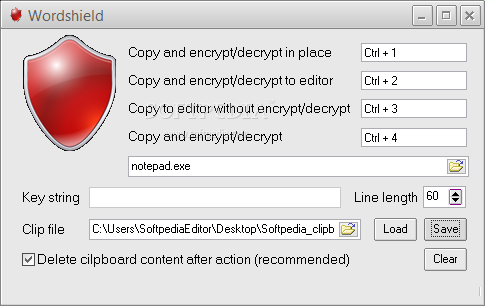
Wordshield
A handy encryption tool that can use an encryption key with the clipboard content so as to make it unreadable until the messages reaches its destinationPrivacy protection is one of the headlines in security-related articles on the Internet and...
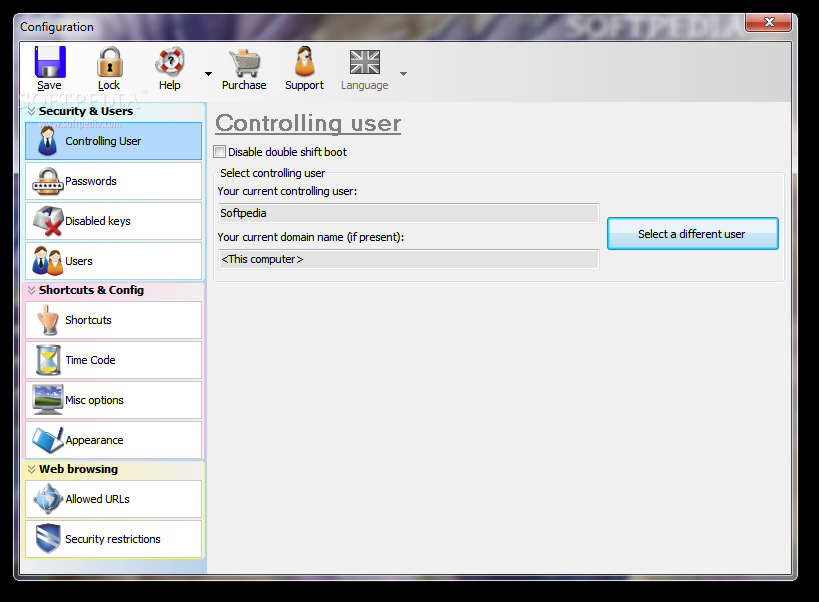
Public PC Desktop
Set up an Internet kiosk or public access PC, block access to vital files, create a list with allowed URLs, disable hotkeys, configure a master password, and generate time-locked codesPublic PC Desktop is a lightweight Windows application designed specifically...
CleanTempShutdown
Tiny and portable utility that cleans up the user temporary folder to free up space and then immediately shuts down your computerHard drives get rapidly filled with data even when you're not trying to download something. Instead, some applications,...
Advanced Internet Kiosk
Create, change and handle various users, configure different Internet and shortcuts settings to offer secure browsing sessions, as well as block unwanted contentAdvanced Internet Kiosk is an accessible and intuitive program designed to provide an easy and efficient method...
Encrypted RunAs
An application which let users run restricted programs without having to make them members of the Power Users or Administrator groupsEncrypted RunAs is a small tool that is created to make the job of Administrators a little easier being...
Exploit Test Tool
Simulates exploit attacks to test the correct functioning of HitmanPro.Alert or check the capabilities of your computer's security softwareExploit Test Toolwas designed to check the correct functioning of HitmanPro.Alert. It simulates different exploit attacks that HitmanPro.Alert should be able...
Crystal Anti-Exploit Protection
Prevents malware from accomodating on your computer.Crystal Anti-Exploit Protection is a handy and reliable utility designed to stop malware from installing itself in your computing environment.Crystal Anti-Exploit Protection allows you to define a list of processes to be monitored...
Malwarebytes Anti-Exploit
Straightforward application with intuitive options that provides a real-time safeguard against vulnerability exploits, catering to all user levels What's new in Malwarebytes Anti-Exploit 1.13.1 Build 186 Beta: Protection: New protection against penetration testing attacks New protection against malicious email...
LinkScanner Lite
Automatically block malicious sites, targeted exploits and zero-day attacks, it scans all pages automatically for true real-time safe browsing protectionThe Internet is filled with all sort of threats and malware that could potentially infect your computer every time you...
Metasploit Community
Penetration testing tool for security professionals that lets them run a discovery scan, bruteforce attack and exploit in order to detect vulnerabilities within a user-defined network rangeMetasploit Community is a professional software application specialized in offering information about security...
INTEL-SA-00075 Detection and Migration Tool
Bespoke utility developed by Intel to help you determine if your computer has been affected by the INTEL-SA-00075 chip vulnerabilityIf you like to stay up to date with the latest computer security news and events, you may know that...

Maui Security Scanner
Maui Security Scanner allows you to scan for specific vulnerabilities, such as Fault Injection, SQL Injection and XSSMaui Security Scanner is an innovative security assessment software suite for today's sophisticated Web application environments..Maui Security Scanner ensures the security of...

HitmanPro.Alert
Cloud-assisted behavioral-based anti-malware solution that secures online banking and shopping, protecting you from software exploits, drive-by downloads, crypto-ransomware, online fraud and identity theftHitmanPro.Alert is a lightweight application able to monitor your browser activity and detect potential threats that may...
Competive Intelligence Toolbar
Competive Intelligence Toolbar is a free and useful toolbarCompetive Intelligence Toolbar is a free and useful toolbar.Here are some key features of "Competive Intelligence Toolbar":■ Free ENCRYPTED communications SOFTWARE, EMAIL, VOIP and IM. ■ Free security systems, proxy tester,...
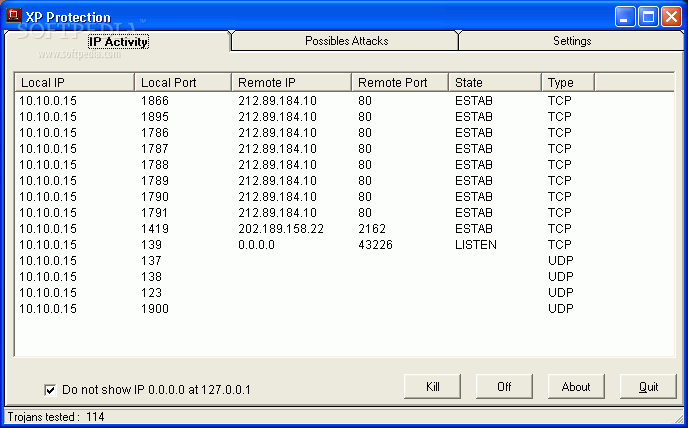
XP Protection
XPProtection provides instant online security in a user-friendly interfaceXPProtection provides security in a user-friendly interface, making you aware of any attacks from hackers, and Trojans.New features include protocol driver level protection, enhanced logging, user selected scan delay, kill on...
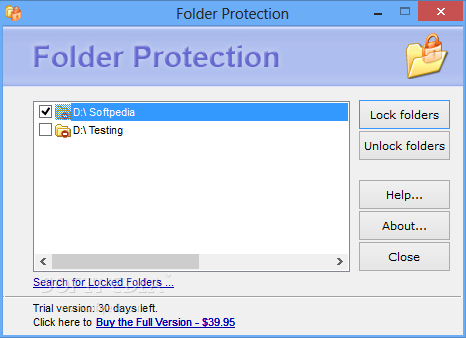
Folder Protection
Prevent access to folders storing sensitive information by easily locking them up with a password straight from their context menuFolder Protection has been created as a simple and uncomplicated solution, thus targeting all types of users that want to...
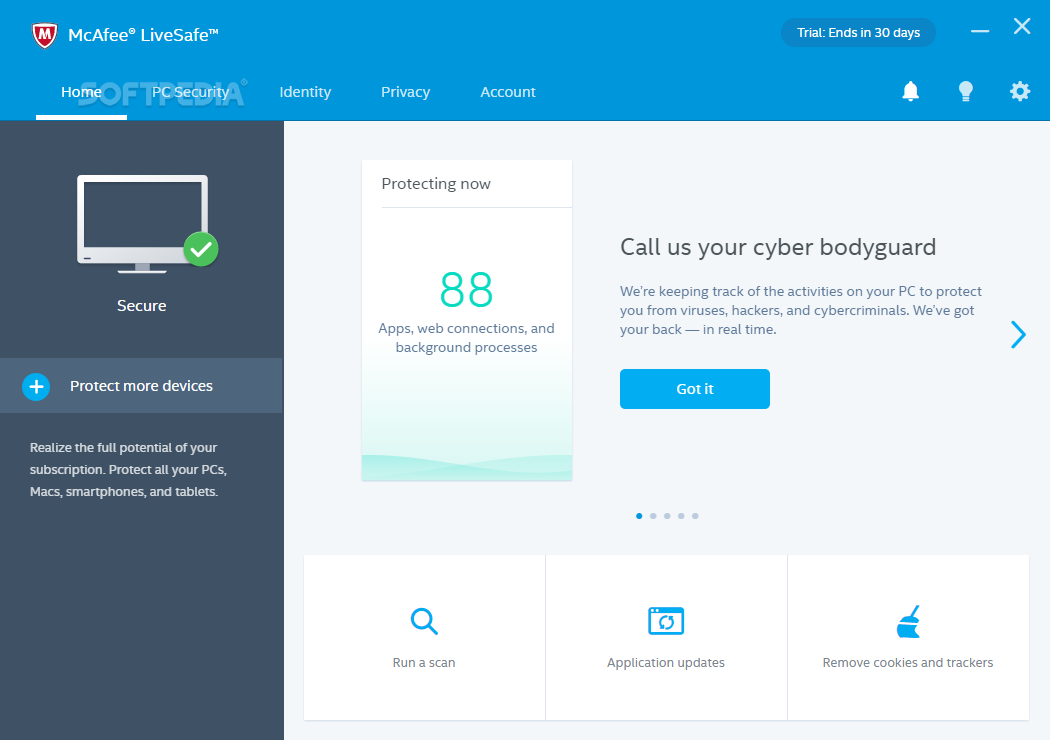
McAfee Total Protection
An effective protection solution against virus, online and network threats, which also features anti-spam and firewall componentsKeeping malware infections at bay by installing a fully-featured antivirus solution on your computer might not prove to be enough to keep your...
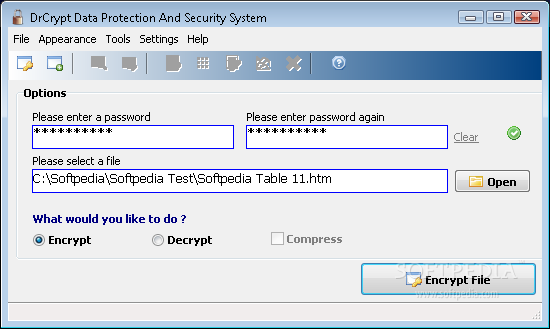
DrCrypt Data Protection and Security System
Secure your files and folders with strong password encryptionDrCrypt, is based our brand-new encryption system which is designed to be fast, reliable and stable. The main difference of DrCrypt from all those similar solutions; fastness and low system resource...
Cyberoam EndPoint Data Protection Suite
Protect your Data. Protect your AssetsCyberoam Endpoint Data Protection protects the organization's endpoints from data leakage through Identity and group-based policy controls, encryption, shadow copies, logging, reporting and archiving. Cyberoam offers data protection and asset management in four easy-to-deploy...
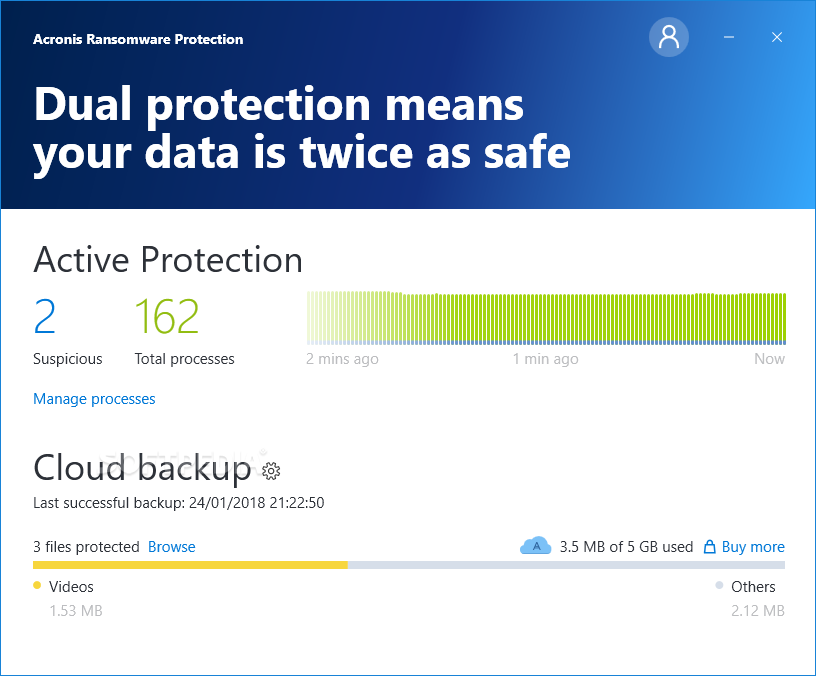
Acronis Ransomware Protection
Monitors active processes on your computer and identifies suspicious ones, allowing you to create whitelists and blacklists to trust or block certain processes What's new in Acronis Ransomware Protection Build 1700: What's new: Issue fixes and other improvements Known...
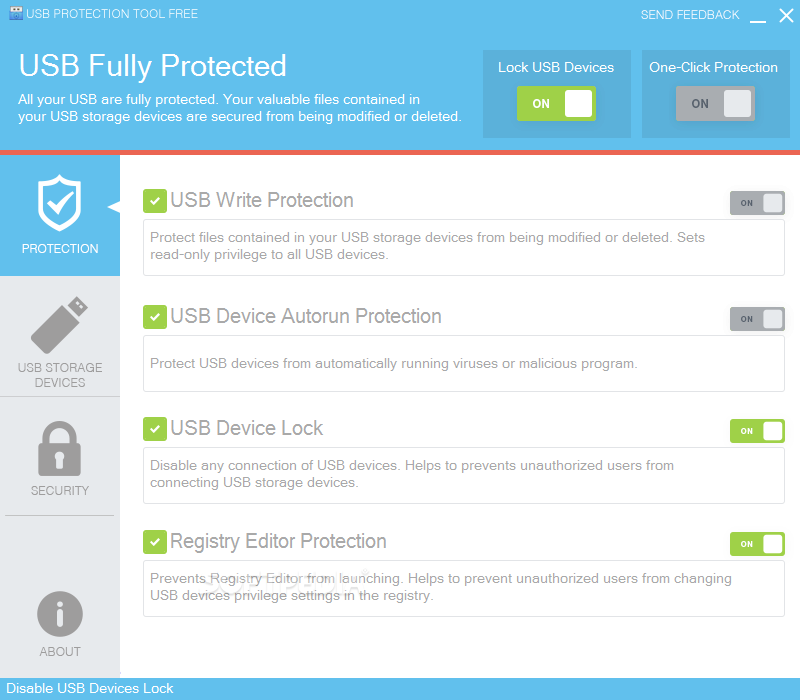
USB Protection Tool
Secure your USB sticks by instituting write and autorun protective measures with this intuitive application that can be password-protected What's new in USB Protection Tool 1.0: Updated: Bugs on Windows 8 Updated: Bugs when reloading drives Added: Password Protection...
McAfee Family Protection
Allows parents to set a collection of rules for preventing exposure to inappropriate content, monitoring the time that children spend onlineMcAfee Family Protection is a promoter of child safety inside the web environment, delivering a set of rules that...
Forefront Endpoint Protection Tools
Use Group Policy for centralized managementThese tools make it easier for Forefront Endpoint Protection 2010 customers to use Group Policy for centralized management, provide optimized settings for various server roles, and diagnose and troubleshoot support issues.FEP Group Policy Tools...
USB Virus Protection
Ensure that autorun.ini viruses commonly found in Flash sticks do not find their way into your computer using this simple and straightforward toolWithout denying the Flash memory sticks can come in handy in numerous occasions, sometimes they can become...
Security Desktop Tool
You can use this software to restrict kids' access to the home PCDesktop Security Tool is a security tool with with you can restrict access to Windows important resources. This easy-to-use application helps you to keep your computer in...
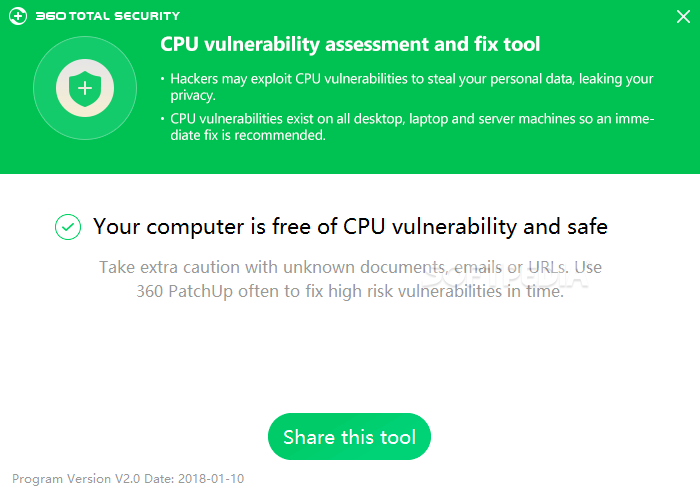
CPU Vulnerability Assessment and Fix Tool
A security tool designed to analyze your PC and discover whether any CPU vulnerabilities exist on your machine, be it a desktop or a serverGoogle's security team revealed important flaws in Intel CPUs in January 2018. Known as Meltdown...
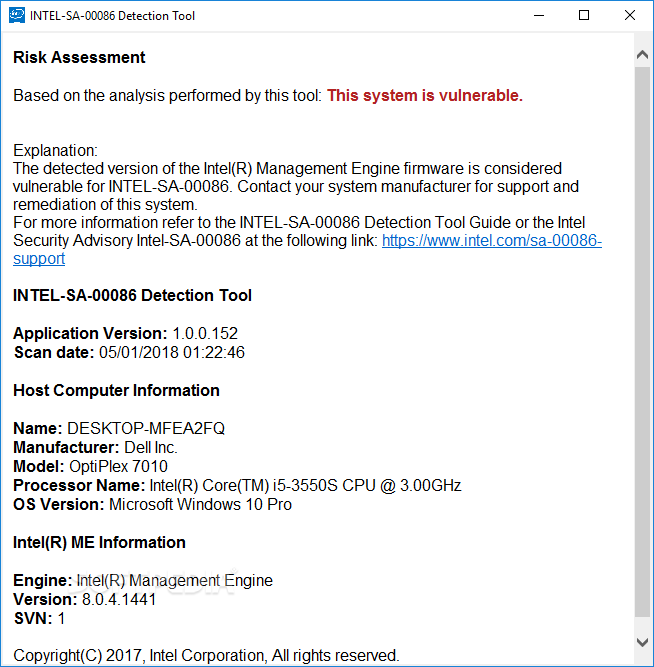
Intel-SA-00086 Detection Tool
A scanning tool specifically designed by Intel to detect whether your system uses one of the firmware versions exposed to the Intel-SA-00086 vulnerabilityFollowing a series of security-related issues reported by outside analysts, Intel conducted a security review of its...
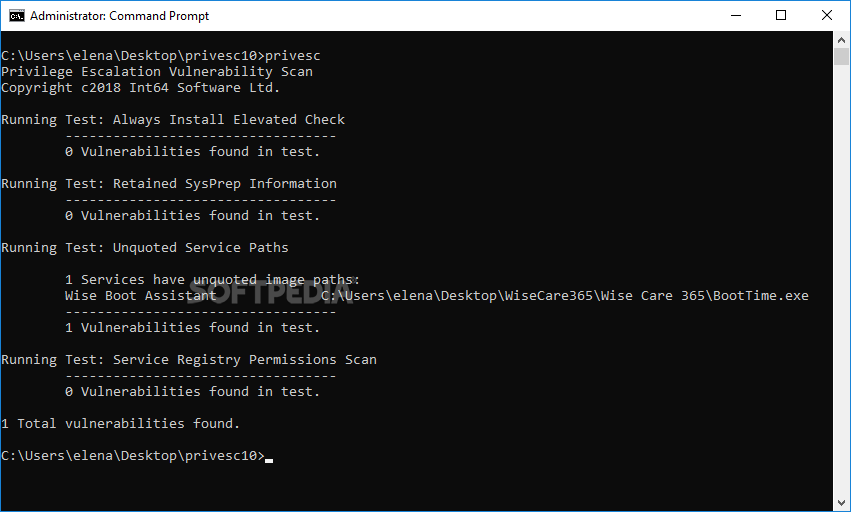
Privilege Escalation Vulnerability Scan Tool
Check common privilege escalation vulnerabilities in Windows using this simple command-line tool that can also scan other workstations in LANTo keep your computer safe from the perils of the web, it's necessary to not only arm it with a...
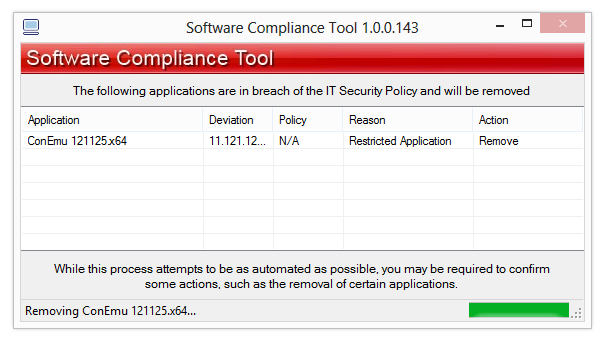
Software Compliance Tool
A very lightweight application created to help reduce the overhead in managing programs that do not belong in a business environment What's new in Software Compliance Tool 1.0.0.149: CHANGE: Default to Report Only Mode (use /REMOVALMODE to actually remove...

AOTop - Ad Obfuscating Tool
A Tool for Visual Privacy ProtectionAOTop - Ad Obfuscating Tool is an application which was created to provide a reliable, automated, , safe, private, and low-cost option of combating the ever-increasing volume blatant commercial advertisement banners appearing unsolicited on your PC...
Avast Decryption Tool for HiddenTear Ransomware
Unlock files that were infected by the HiddenTear ransomware and recover your data without having to pay a dime to the cybercriminalsHiddenTear is the famous open-source ransomware whose author published the code on GitHub as a proof-of-concept and an...