BN+ Brute Force Hash Attacker Alternatives for Windows
Do you want to find the best BN+ Brute Force Hash Attacker alternatives for Windows? We have listed 30 Security that are similar to BN+ Brute Force Hash Attacker. Pick one from this list to be your new BN+ Brute Force Hash Attacker app on your computers. These apps are ranked by their popularity, so you can use any of the top alternatives to BN+ Brute Force Hash Attacker on your computers.
Top 30 Software Like BN+ Brute Force Hash Attacker - Best Picks for 2025
The best free and paid BN+ Brute Force Hash Attacker alternatives for windows according to actual users and industry experts. Choose one from 30 similar apps like BN+ Brute Force Hash Attacker 2025.
MD5 Brute Force Tool
Simple but powerful command-line utility that helps you test the MD5 checksums of your files using brute force, by specifying the alphabet and maximum lengthMD5 Brute Force Tool is a command-line application designed for users who want to verify...
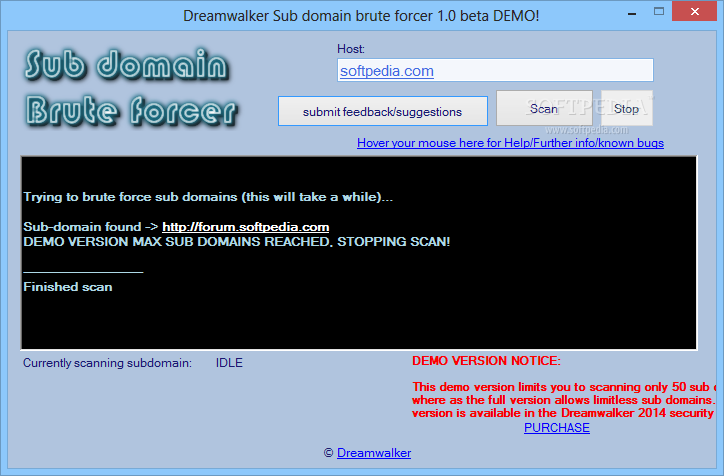
Dreamwalker Sub domain brute forcer
Aiming to test the reliability and security of your web server, this application can simulate a brute forcing attack to retrieve a host's sub-domainsDreamwalker Sub domain brute forcer can prove to be a handy tool in the hands of...
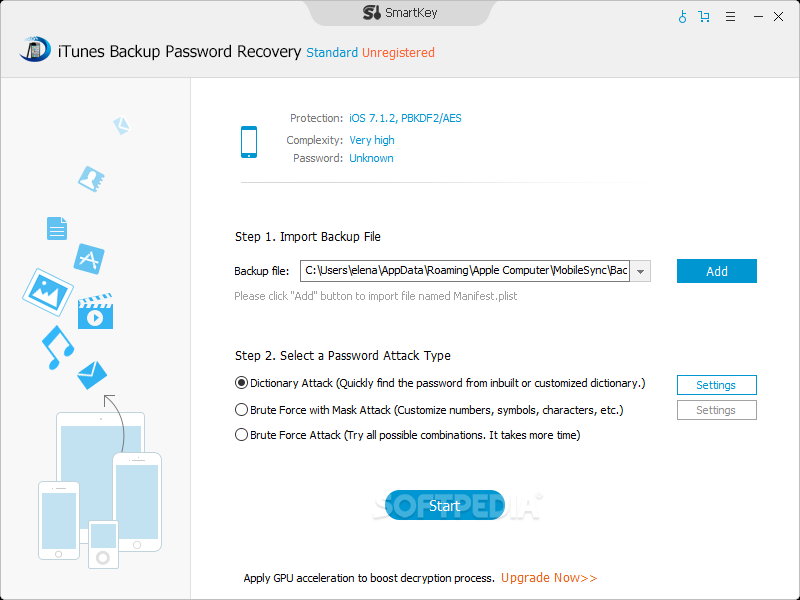
iTunes Backup Password Recovery
Try to decrypt your lost or forgotten iTunes backup passwords using dictionary or brute force with the help of this software tooliTunes Backup Password Recovery is an application that promises to find out the lost or forgotten passwords of...
DirBuster
Find files and folders on web/application servers left behind by developers using brute force, and configure a wide range of settings What's new in DirBuster 1.0 RC1: Auto pause, when 20 consecutive 20 errors happen Spelling mistakes corrected Multi...
Solway's Password Recover
Seamlessly retrieve lost or forgotten passwords to personal RAR or ZIP archives by using dictionary or brute force attack methodsWith the help of Solway's Password Recover you can try to find out the passwords to ZIP or RAR archives,...
Bruter
Simple tool that can demonstrate the importance of enabling strong passwords for targets with sensitive content by running brute-force attacksA weak countersign is for an attacker like a free invitation to accessing sensitive information but a strong one, although...
Free RAR Password Unlocker
Unlock encrypted archived files, with this application, that is capable of using brute force, masked brute force or dictionary attacksFree RAR Password Unlockeris a powerful application designed to decrypt password protected archive files. It can be a suitable solution...
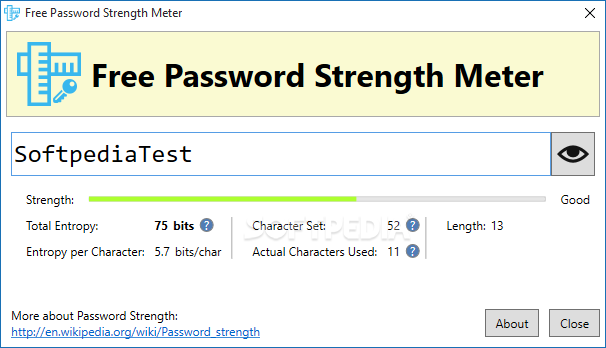
Free Password Strength Meter
Check the strength of your password, verify its entropy level and make sure no brute-force attack application will be able to break itThe majority of computer users build their passwords using words and numbers they can easily remember, but...
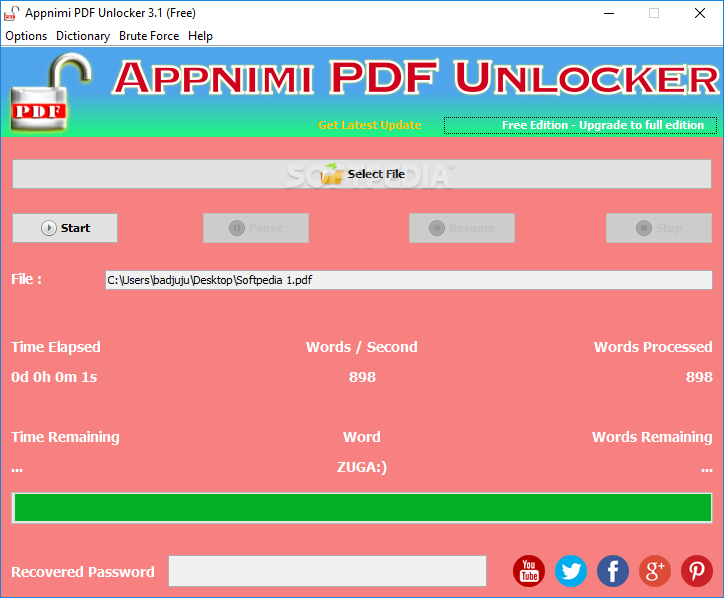
Appnimi PDF Unlocker
Recover lost or forgotten PDF passwords using the dictionary or brute force attack mode provided by this application with simple optionsAppnimi PDF Unlocker is an intuitive application that attempts to unlock password-protected PDF documents using one of the two...
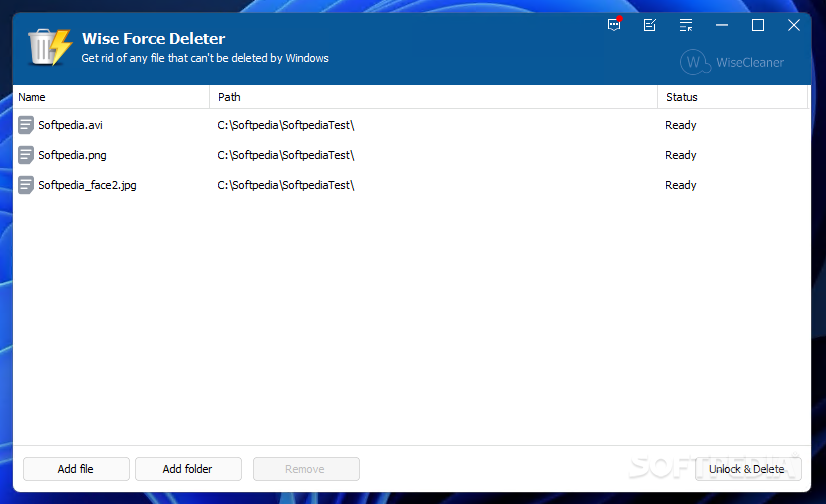
Wise Force Deleter
Permanently erase files on your computer, even if they are used by other applications or access to them is denied without administrator rights What's new in Wise Force Deleter 1.5.2.53: Minor bug fixes. Updated various translations. GUI and usability...

Money Password
Retrieve lost or forgotten passwords from MS Money files (MNY and MBF file format) using several advanced recovery methods, such as Brute Force Attack, Dictionary Attack, and Smart Force AttackMoney Passwordis a small software application whose purpose is to...
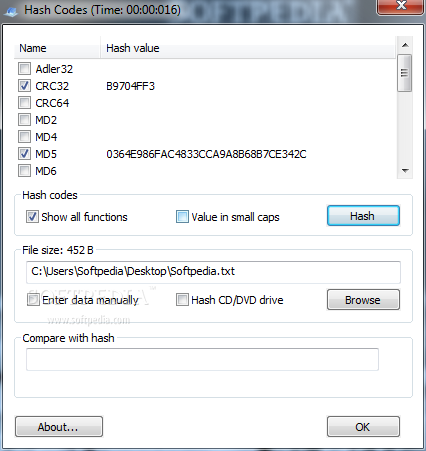
Hash Codes
Straightforward application which enables you to easily calculate various hash algorithms for any file from the HDD, CD, DVD or body textHash Codes is a software tool which was developed specifically to aid people in generating checksums for many...
Hash Kracker Console
A command-line application that enables you to recover your lost encrypted passwords and bypass the hash sequence that protects them What's new in Hash Kracker Console 2.0: Integrated Uninstaller into Windows Add/Remove Programs, now you can uninstall it in...
Hash Suite
Make sure Windows account passwords can withstand powerful attacks by testing them out with several test cases based on the password hash What's new in Hash Suite 3.5.1: Fix bug on Hashes_found report. Other minor bug fixes and enhancements....
File Hash Generator
Compute and save hashes for batches of files, according to the selected algorithm MD5, SHA1, SHA-256, SHA-512 CRC-16 or RIPEMD-160File Hash Generator allows you to quickly view the hashes of large groups of files, which you can manually load...
Fenix Hash Checker
A simple to use application dedicated to calculating the checksums of two files and compare them or analyzing the provided hashesFenix Hash Checkeris a reliable software that enables you to compare two files and determine whether they are identical...
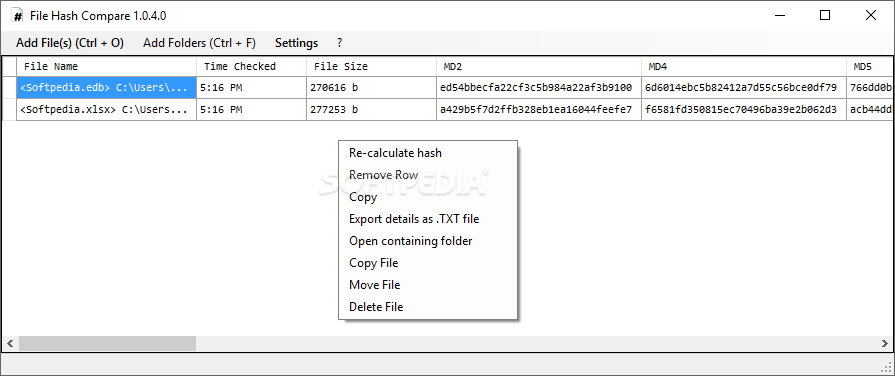
File Hash Compare
View a file's checksum, generated according to several algorithms, then compare it to other items' in order to verify its integrity What's new in File Hash Compare 1.0.4.1: General UI improvements Bug fixes Read the full changelog File...
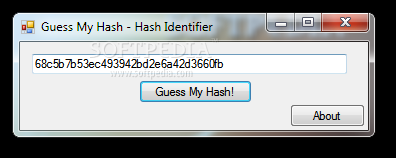
Guess my Hash - Hash Identifier
A simple-to-use yet efficient software application that helps you identify hash types (e.g. MD5, NTLM, MySQL) based on a user-defined codeGuess my Hash - Hash Identifier is a lightweight software application built specifically for helping you identify possible hash...
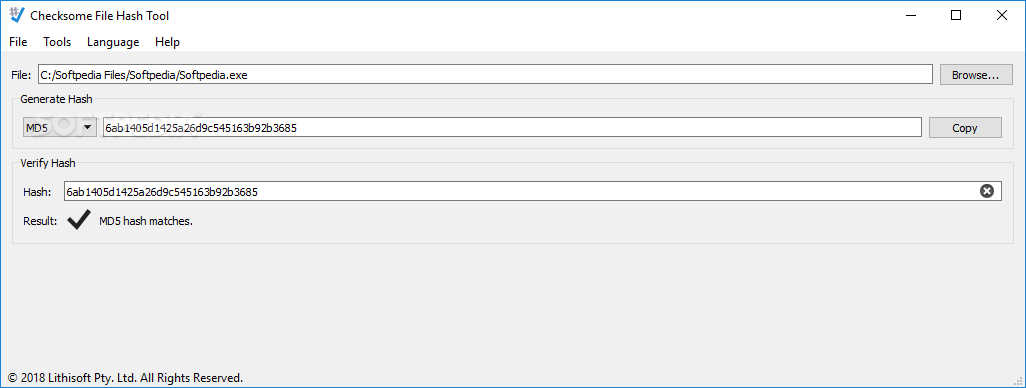
Checksome File Hash Tool
Generates various hash codes for the selected file and enables you to verify the file integrity by comparing the generated hash with a specific code What's new in Checksome File Hash Tool 1.2: Application no longer in beta. ...
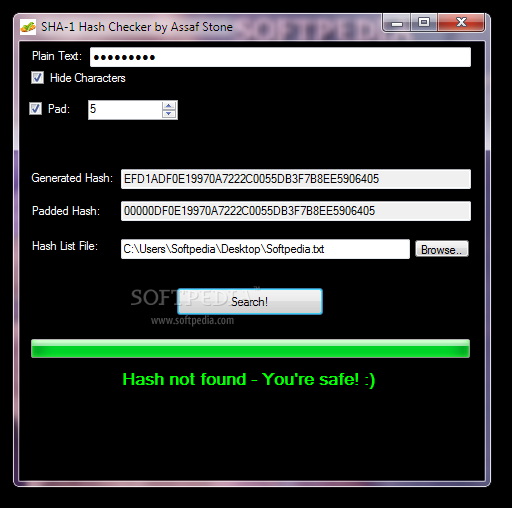
SHA-1 Hash Checker
Verify the integrity of your passwords via hash checks by specifying a custom password and loading a hash list file, with the aid of this portable toolSHA-1 Hash Checker is a security application whose purpose is to help you...
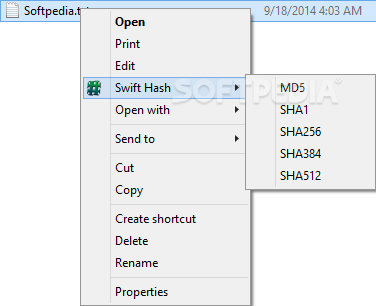
Swift Hash
With this simple and effective utility, you can calculate a file's hash in MD5, SHA1, SHA512 and others, just by right-clicking itSwift Hash is an intuitive and straightforward piece of software whose main purpose resides in helping you determine...

Maui Security Scanner
Maui Security Scanner allows you to scan for specific vulnerabilities, such as Fault Injection, SQL Injection and XSSMaui Security Scanner is an innovative security assessment software suite for today's sophisticated Web application environments..Maui Security Scanner ensures the security of...
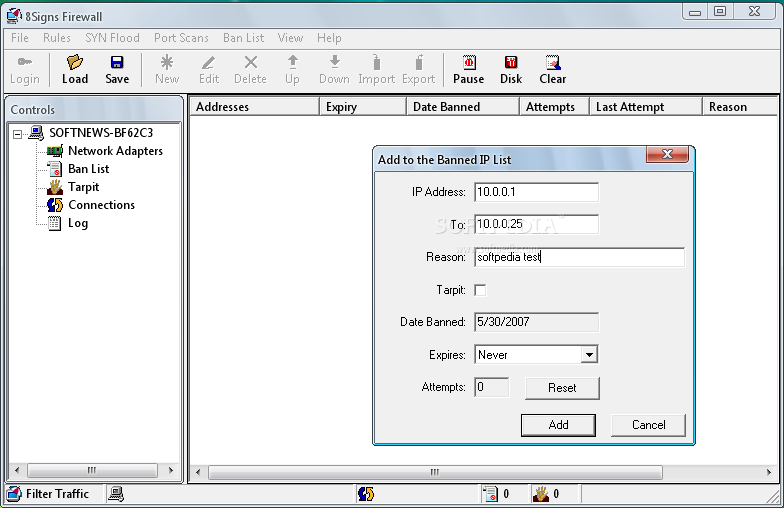
8Signs Firewall
protect a Windows Internet server, complete information and control over network security What's new in 8Signs Firewall 3.02: Fixed bug that could cause the firewall to crash if the user attempted to sort an IP Address Group Read...

Socket Security Auditor
Identifies the insecurely bound socketsApplication developers need to be aware that attackers can target these same client-server applications by "hijacking" the server socket. Insecurely bound server sockets allow an attacker to bind his / her own socket on the...
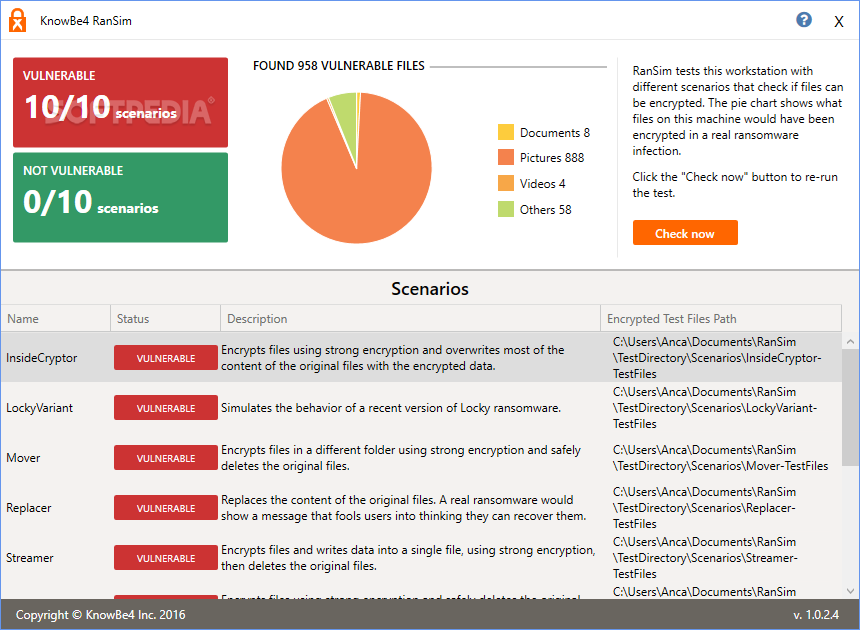
RanSim
Carry out simulations of ransomware attacks with the help of this easy-to-use software utility that can test your PC's security in 10 different infection scenariosBeing ahead of the curve with security measures is not an easy thing to do,...
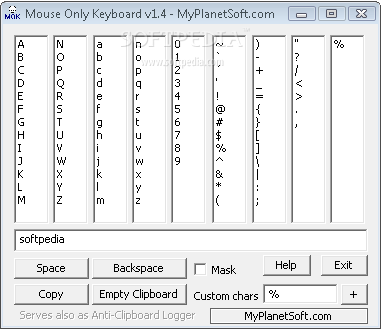
Mouse Only Keyboard
Write down passwords and other sensitive text that can be tracked down by keyloggers without using your keyboard thanks to this practical utilityEveryone’s spying on everyone, or at least trying. Methods can be pretty cunning, ingenious, or plain dumb...
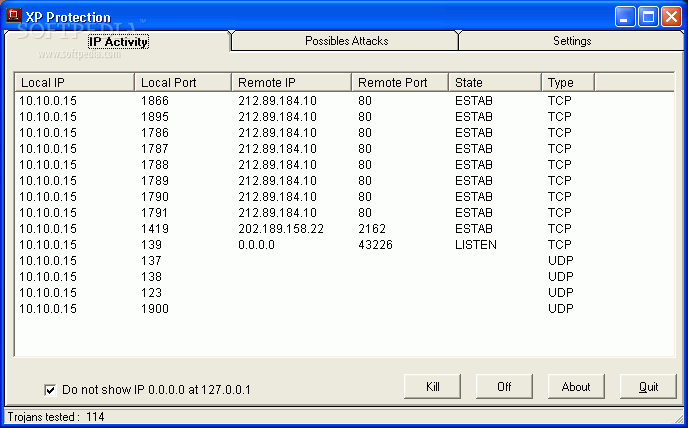
XP Protection
XPProtection provides instant online security in a user-friendly interfaceXPProtection provides security in a user-friendly interface, making you aware of any attacks from hackers, and Trojans.New features include protocol driver level protection, enhanced logging, user selected scan delay, kill on...
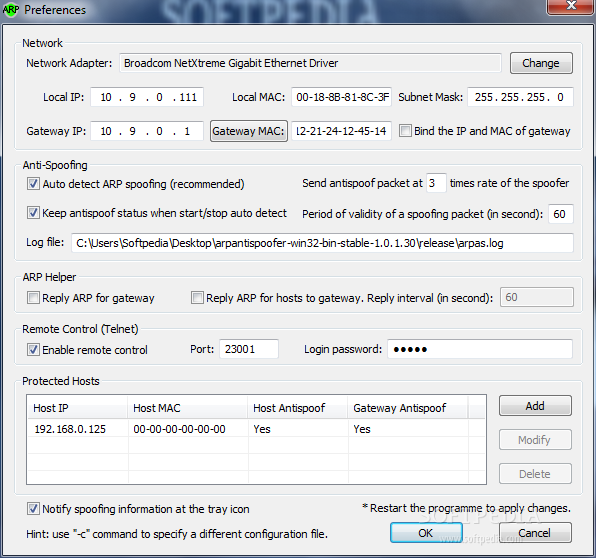
ARP AntiSpoofer
A simple to use piece of software that is capable of detecting bidirectional ARP spoofing and making sure that your computer is safeSpoofing, is a means in which someone can hide an application or command that is meant to...
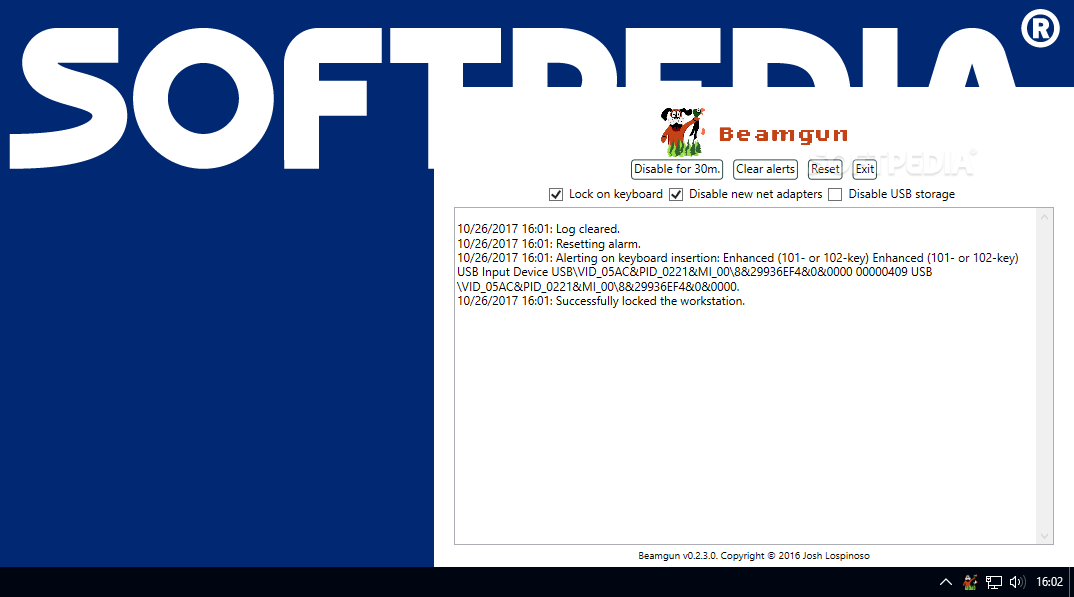
Beamgun
Protect your PC against rogue USB devices such as the USB Rubber Ducky and LAN Turtle, which can inject keystrokes and compromise sensitive information What's new in Beamgun 0.2.4: Fixed bug with portable .exe not starting under certain circumstances...