MD5 Brute Force Tool Alternatives for Windows
Do you want to find the best MD5 Brute Force Tool alternatives for Windows? We have listed 31 Security that are similar to MD5 Brute Force Tool. Pick one from this list to be your new MD5 Brute Force Tool app on your computers. These apps are ranked by their popularity, so you can use any of the top alternatives to MD5 Brute Force Tool on your computers.
Top 31 Software Like MD5 Brute Force Tool - Best Picks for 2025
The best free and paid MD5 Brute Force Tool alternatives for windows according to actual users and industry experts. Choose one from 31 similar apps like MD5 Brute Force Tool 2025.
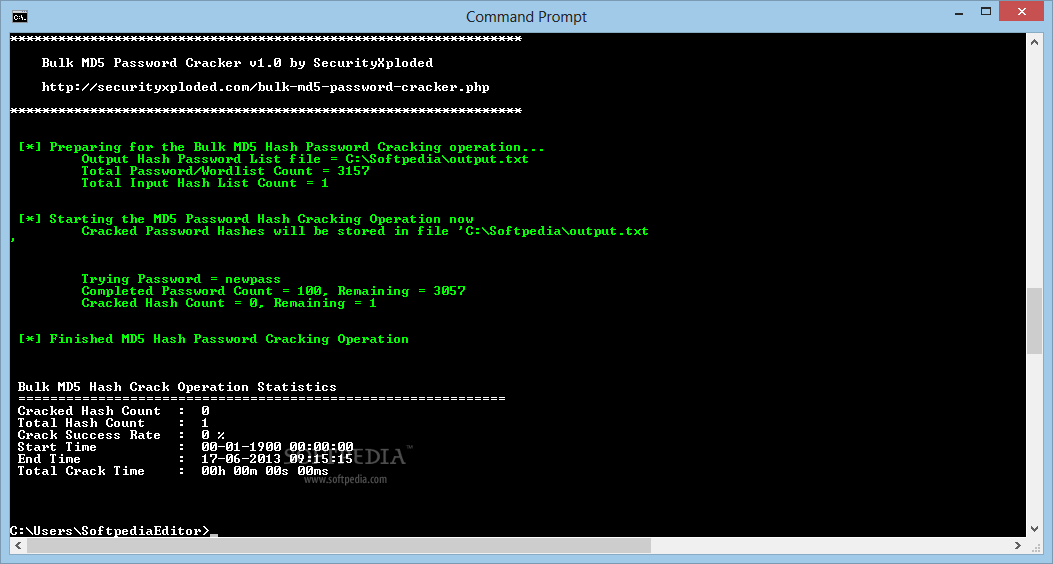
Bulk MD5 Password Cracker
Recover passwords from MD5 checksums by using a customizable dictionary file and saving results to TXT with this simple command line tool What's new in Bulk MD5 Password Cracker 3.0: Mega 2016 release with support for new Windows 10...
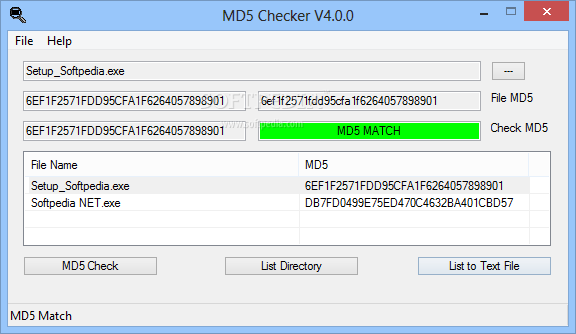
MD5 Checker
This utility is especially designed for generating MD5 checksums, verifying them as well as listing the file hashes into a documentFiles are verified by your computer when launched, or whenever a download is done. Complex algorithms are used to...
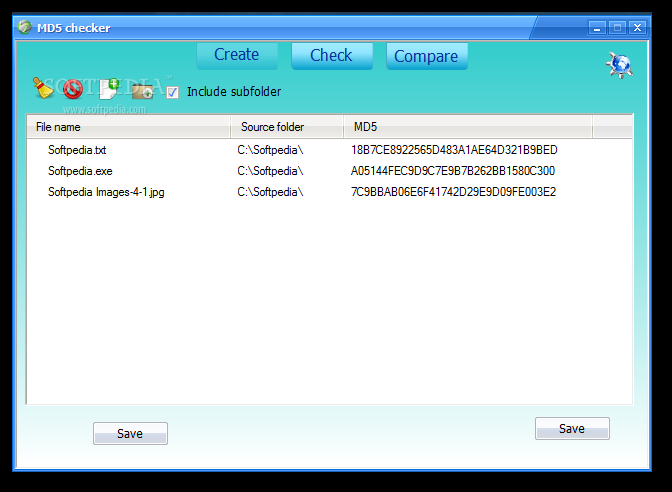
MD5 checker
Calculate and compare MD5 checksums, as well as create and verify MD5-formatted files using this intuitive and portable applicationMD5 checker is a feather-light and portable utility that gives you the possibility to put together MD5 files with the MD5...
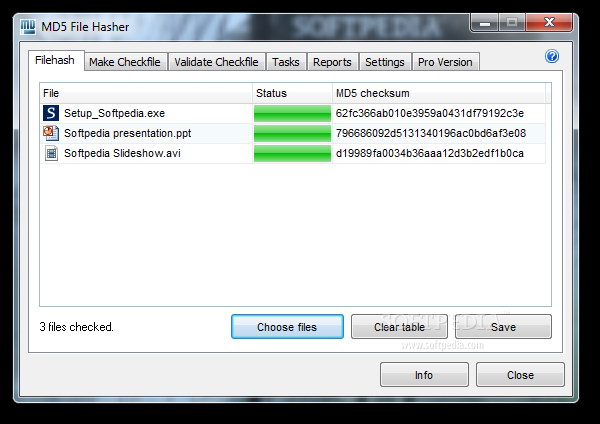
MD5 File Hasher
Advanced MD5 checksum tool to validate file integrity in batch mode, create checkfiles, schedule repetitive tasks, and generate reportsMD5 File Hasher is an advanced software utility that you can use to verify the integrity of your files in batch...
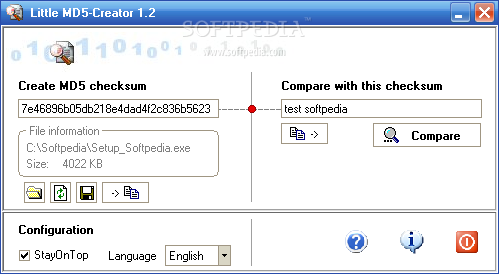
Little MD5-Creator
Makes MD5 checksums of any files What's new in Little MD5-Creator 1.2: Helpfile updated New version of UPXG (for packing the executable) Setup file is now generated with NSIS License agreement updated Read the full changelog Little MD5-Creator...
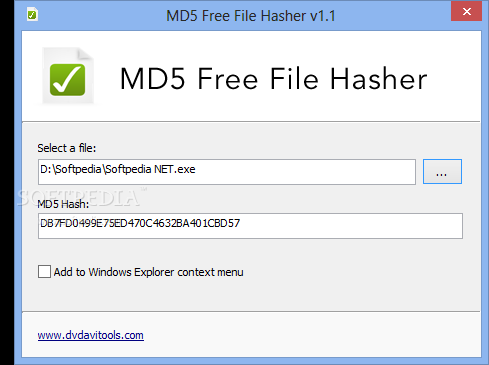
MD5 Free File Hasher
Effortlessly calculate MD5 file checksums using this straightforward tool that can be integrated with the Explorer right-click menu What's new in MD5 Free File Hasher 1.2.0.0: Added support for Drag & Drop Read the full changelog Checksums are...
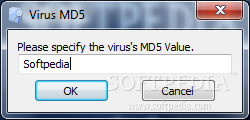
MD5 Virus search and cleaner
Scans the computer to identify and automatically delete files infected with various malware agents after specifying their MD5 hashesMD5 Virus search and cleaner is a lightweight software application that can be configured to locate and eliminate files infected with...

MD5 Calculator
Calculate and compare MD5 signatures to check file integrity using this intuitive app optimized for PCs and tablets running Windows 8 and 8.1 What's new in MD5 Calculator 1.2.0.0: Fixed Snapped View on low resolution screen Read the...
MD5 Multiple Files
Calculate MD5 file values and compare them, process multiple files simultaneously, and drag and drop items directly in the main windowMD5 Multiple Files is a small software application whose purpose is to help you verify the integrity of files...
Dreamwalker Sub domain brute forcer
Aiming to test the reliability and security of your web server, this application can simulate a brute forcing attack to retrieve a host's sub-domainsDreamwalker Sub domain brute forcer can prove to be a handy tool in the hands of...
BN+ Brute Force Hash Attacker
Recover your passwords with this utility by one of the most popular decryption technologies in the world: the brute force attackBN+ Brute Force Hash Attacker provides users with an application software to help you recover collected passwords within hash...
iTunes Backup Password Recovery
Try to decrypt your lost or forgotten iTunes backup passwords using dictionary or brute force with the help of this software tooliTunes Backup Password Recovery is an application that promises to find out the lost or forgotten passwords of...
DirBuster
Find files and folders on web/application servers left behind by developers using brute force, and configure a wide range of settings What's new in DirBuster 1.0 RC1: Auto pause, when 20 consecutive 20 errors happen Spelling mistakes corrected Multi...
Solway's Password Recover
Seamlessly retrieve lost or forgotten passwords to personal RAR or ZIP archives by using dictionary or brute force attack methodsWith the help of Solway's Password Recover you can try to find out the passwords to ZIP or RAR archives,...
Bruter
Simple tool that can demonstrate the importance of enabling strong passwords for targets with sensitive content by running brute-force attacksA weak countersign is for an attacker like a free invitation to accessing sensitive information but a strong one, although...
Free RAR Password Unlocker
Unlock encrypted archived files, with this application, that is capable of using brute force, masked brute force or dictionary attacksFree RAR Password Unlockeris a powerful application designed to decrypt password protected archive files. It can be a suitable solution...
Free Password Strength Meter
Check the strength of your password, verify its entropy level and make sure no brute-force attack application will be able to break itThe majority of computer users build their passwords using words and numbers they can easily remember, but...
Appnimi PDF Unlocker
Recover lost or forgotten PDF passwords using the dictionary or brute force attack mode provided by this application with simple optionsAppnimi PDF Unlocker is an intuitive application that attempts to unlock password-protected PDF documents using one of the two...
Wise Force Deleter
Permanently erase files on your computer, even if they are used by other applications or access to them is denied without administrator rights What's new in Wise Force Deleter 1.5.2.53: Minor bug fixes. Updated various translations. GUI and usability...

Money Password
Retrieve lost or forgotten passwords from MS Money files (MNY and MBF file format) using several advanced recovery methods, such as Brute Force Attack, Dictionary Attack, and Smart Force AttackMoney Passwordis a small software application whose purpose is to...
Security Desktop Tool
You can use this software to restrict kids' access to the home PCDesktop Security Tool is a security tool with with you can restrict access to Windows important resources. This easy-to-use application helps you to keep your computer in...
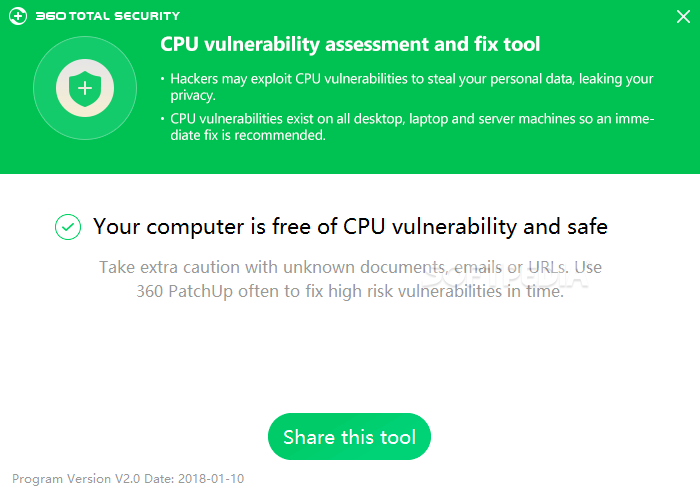
CPU Vulnerability Assessment and Fix Tool
A security tool designed to analyze your PC and discover whether any CPU vulnerabilities exist on your machine, be it a desktop or a serverGoogle's security team revealed important flaws in Intel CPUs in January 2018. Known as Meltdown...
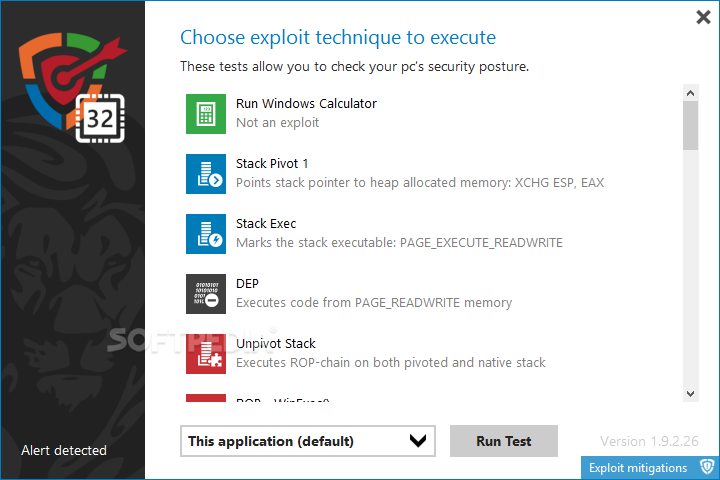
Exploit Test Tool
Simulates exploit attacks to test the correct functioning of HitmanPro.Alert or check the capabilities of your computer's security softwareExploit Test Toolwas designed to check the correct functioning of HitmanPro.Alert. It simulates different exploit attacks that HitmanPro.Alert should be able...
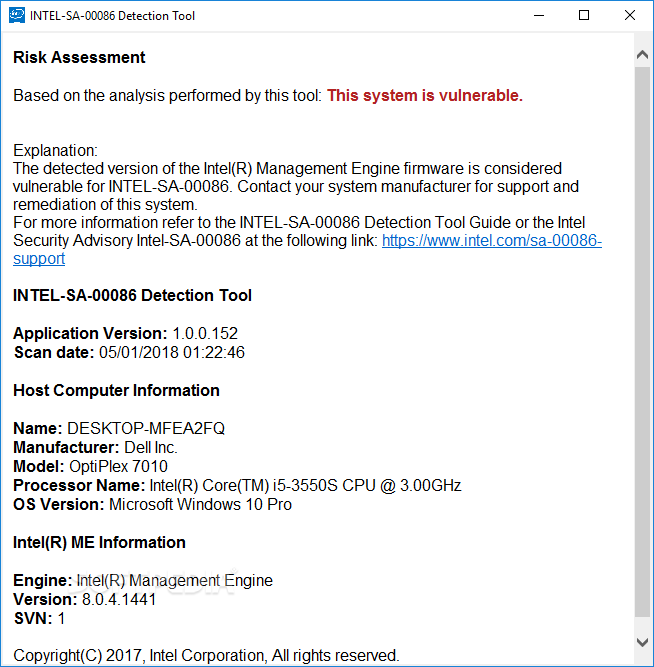
Intel-SA-00086 Detection Tool
A scanning tool specifically designed by Intel to detect whether your system uses one of the firmware versions exposed to the Intel-SA-00086 vulnerabilityFollowing a series of security-related issues reported by outside analysts, Intel conducted a security review of its...
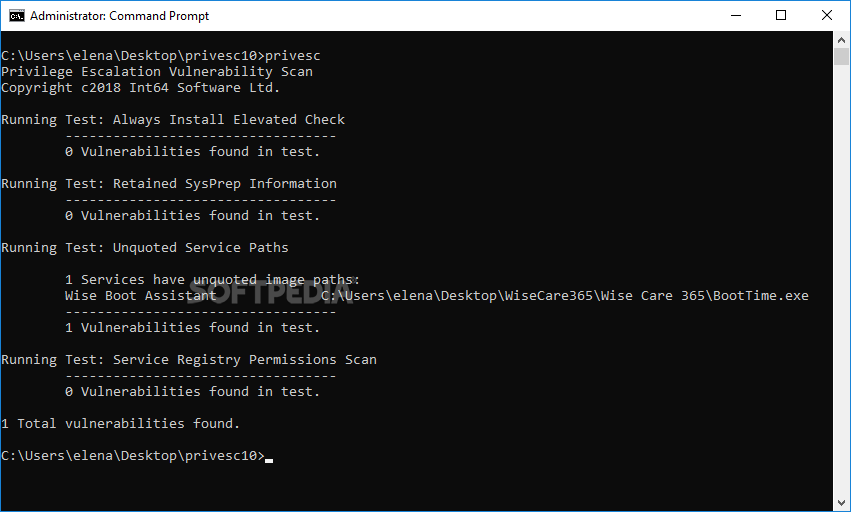
Privilege Escalation Vulnerability Scan Tool
Check common privilege escalation vulnerabilities in Windows using this simple command-line tool that can also scan other workstations in LANTo keep your computer safe from the perils of the web, it's necessary to not only arm it with a...
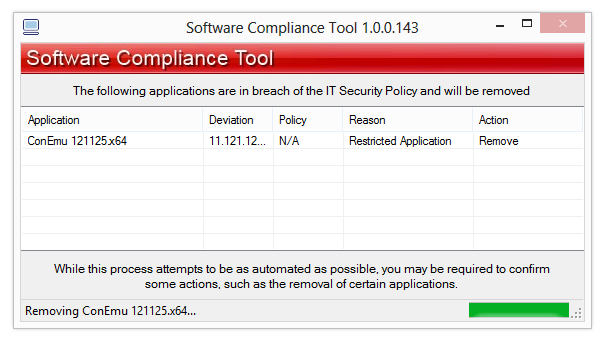
Software Compliance Tool
A very lightweight application created to help reduce the overhead in managing programs that do not belong in a business environment What's new in Software Compliance Tool 1.0.0.149: CHANGE: Default to Report Only Mode (use /REMOVALMODE to actually remove...
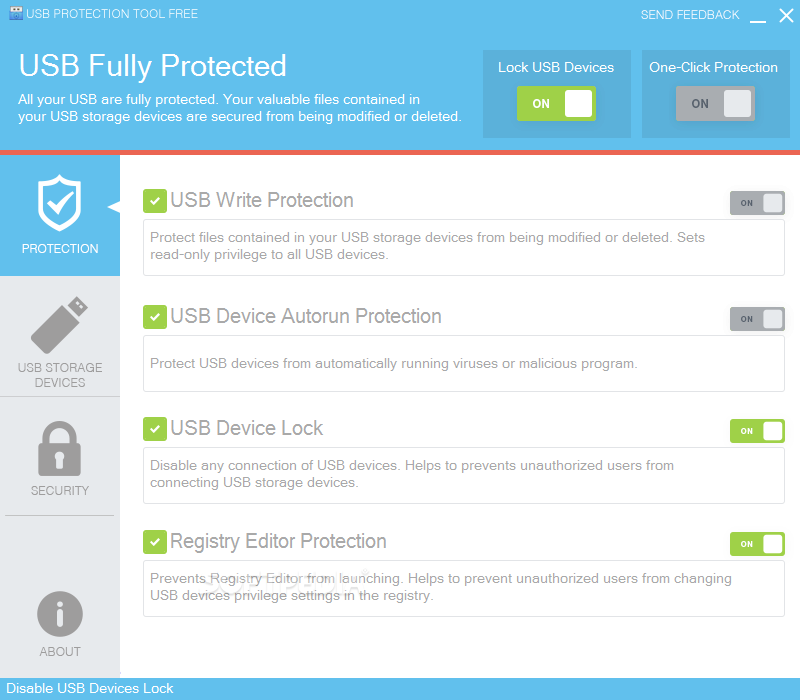
USB Protection Tool
Secure your USB sticks by instituting write and autorun protective measures with this intuitive application that can be password-protected What's new in USB Protection Tool 1.0: Updated: Bugs on Windows 8 Updated: Bugs when reloading drives Added: Password Protection...
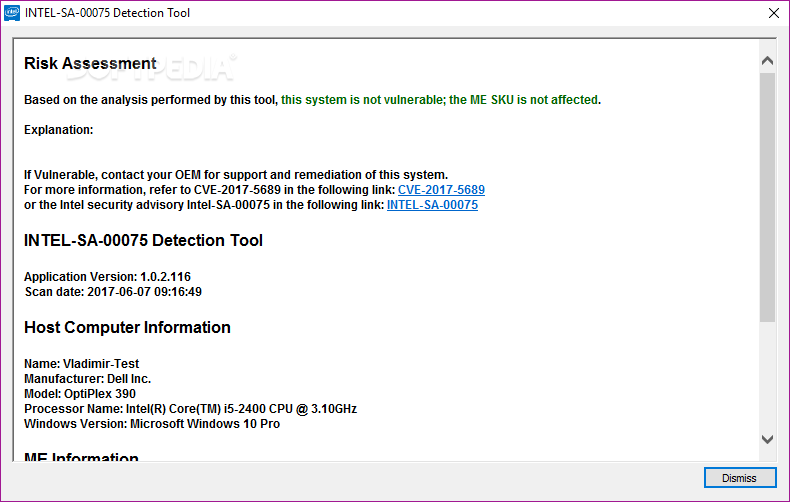
INTEL-SA-00075 Detection and Migration Tool
Bespoke utility developed by Intel to help you determine if your computer has been affected by the INTEL-SA-00075 chip vulnerabilityIf you like to stay up to date with the latest computer security news and events, you may know that...

AOTop - Ad Obfuscating Tool
A Tool for Visual Privacy ProtectionAOTop - Ad Obfuscating Tool is an application which was created to provide a reliable, automated, , safe, private, and low-cost option of combating the ever-increasing volume blatant commercial advertisement banners appearing unsolicited on your PC...
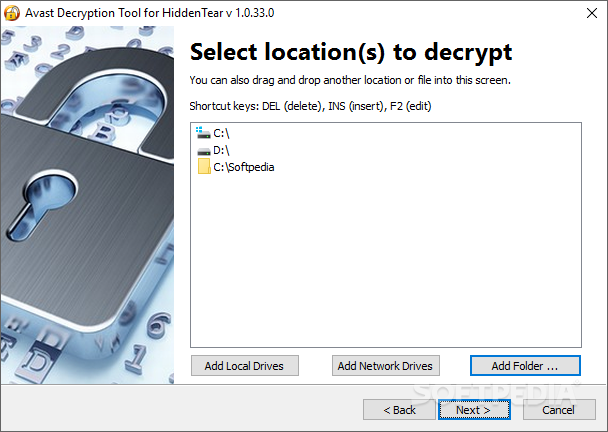
Avast Decryption Tool for HiddenTear Ransomware
Unlock files that were infected by the HiddenTear ransomware and recover your data without having to pay a dime to the cybercriminalsHiddenTear is the famous open-source ransomware whose author published the code on GitHub as a proof-of-concept and an...